Public Services and Procurement Canada, oversees how the government buys goods and services, and has different levels of security clearance depending on whether a contractor has access to classified information. You know what’s worse than fighting an active breach… being breached and not knowing it.
Public Services and Procurement Canada, oversees how the government buys goods and services, and has different levels of security clearance depending on whether a contractor has access to classified information. You know what’s worse than fighting an active breach… being breached and not knowing it.
With so many security controls available today you’d think the likelihood of a government breach would be next to zero, but sadly it is as likely now as ever before. Since most of most government security teams’ budget goes to blocking threats from the outside, it’s no wonder attackers, once in your environment, are so successful. They take advantage of the blind spots that exist in most of the government networks, and they are pretty good at it.
“The government of Canada does go a long way to do that when there is sensitive information in play. When there’s no sensitive information at play, companies do need to realize that this is a growing [trend],” says Dr. Bill Pomfret A spokesperson for Public Services and Procurement Canada said the department is working to ensure all companies are properly vetted.
“Ransomware and the impacts of this type of attack are monitored by Public Services and Procurement Canada in collaboration with other government security agencies,” said spokesperson Stéfanie Hamel. “Public Services and Procurement Canada is working closely with relevant departmental stakeholders to ensure that, as part of the procurement process, companies it does business with have gone through intensive screening and meet all of our security requirements before any contract is granted.” Words one would expect from a Civil Service spokesperson,
A Montreal-based aerospace company contracted to the military has suffered a crippling cyberattack – one that the government is trying to determine the extent of. The Department of National Defense (DND) confirmed last month that the vendor in question, CMC Electronics, alerted the government that it had sustained a “cyber breach related incident” in May.
According to procurement records, CMC had done millions in work for the Canadian Armed Forces, mainly in engineering and research development. DND noted that CMC had been contracted for such work for approximately $19.5 million since 2011. Most of the contracts, about 66, were for research and development of engineering services. News of the hacking comes after the federal government announced on May 30 that CMC would participate in a joint $800 million job to upgrade Canada’s 85 CH-146 Griffon helicopters.
“DND/CAF does not comment on the cyber or IM/IT approaches of third-party vendors; however, we recognize the importance of cyber security in defence and defence contracting,” a DND spokesperson told Global News.
The spokesperson also gave assurances that none of DND’s internal systems employ CMC Electronics technology, adding that the department is “continuing to monitor” the situation while ensuring both CAF and its own information is safeguarded. CMC Electronics has reached out to Insurance Business to confirm that the incident has been contained
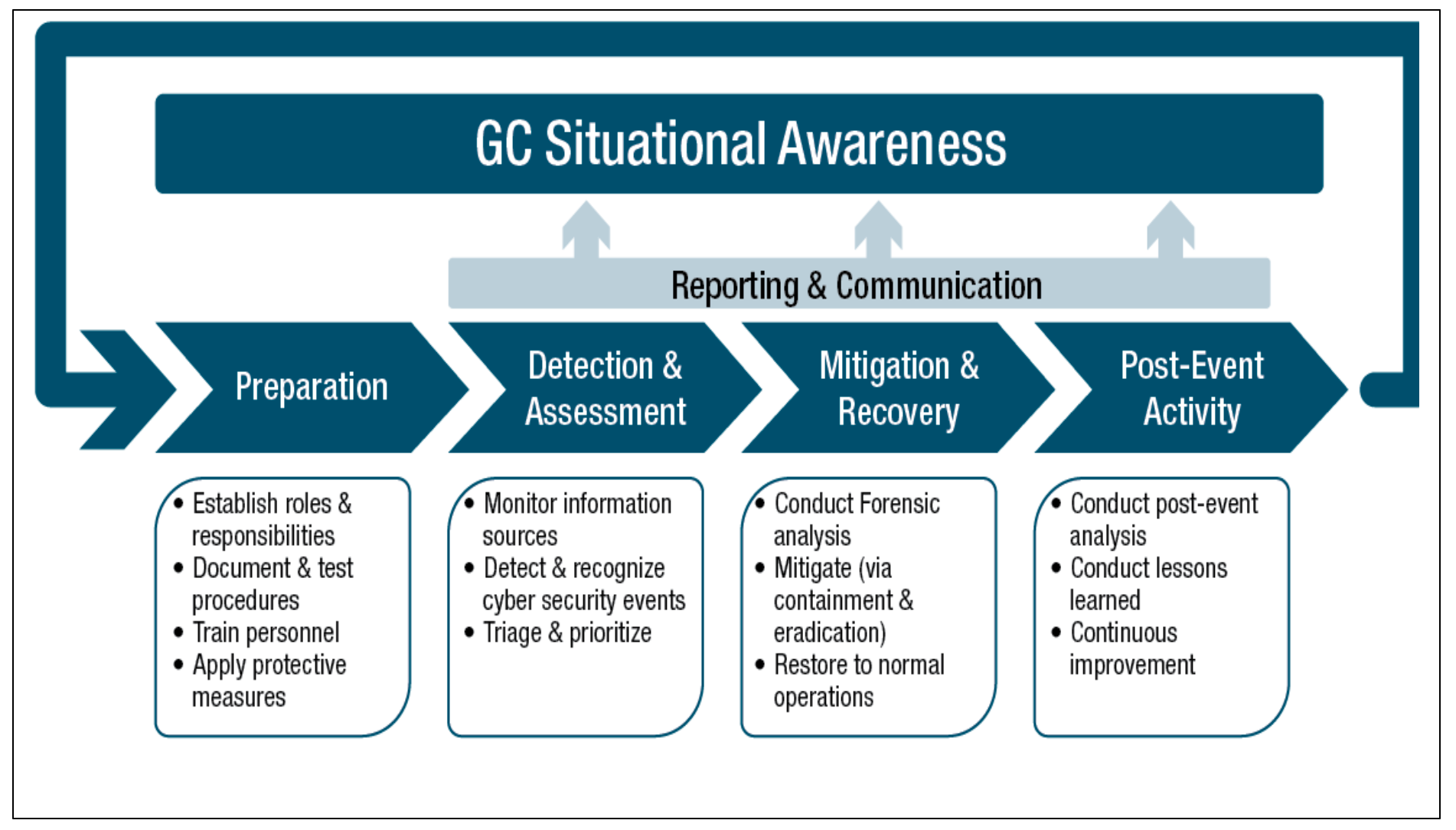
Government of Canada Cyber Security Event Management Plan
“On May 31, 2022, CMC Electronics (CMC) identified that an unauthorized third-party had gained access to our computer network and disrupted our operations in connection with a ransom demand. We proactively took steps to shut down our network to protect our systems and data. At this stage, we are confident that we have successfully contained the incident,” the company said in an email statement.
CMC also confirmed in its statement that it has launched an investigation into the matter with “the assistance of outside cybersecurity experts,” which includes “leading forensics specialists,” and that it had reported the incident to relevant authorities.
“CMC takes the security of our systems and our customers’ data extremely seriously, and we regret any concern or inconvenience this incident may cause,” the company prefaced.
While there is no indication to date that those responsible for the cyberattack have stolen any sensitive military information, other public reports have suggested that the malware attack was allegedly carried out by a ransomware gang known as “ALPHV” or “BlackCat.” An intelligence source who asked to remain anonymous said that it is believed that the ransomware group’s technology was developed by another group that has direct links to Moscow.
Cyber attacks can have a significant effect, both internally and on prospects of winning work. investigates what can be done to minimise this disruption and looks at why openness and transparency is being urged in this often-secretive element of business risk.
On 4 May, Royal Bam group director of cyber security Ian Hill got a call at midnight from a member of his team, telling him Bam Construct’s systems were under attack. Hackers had found what he describes as “a very obscure” vulnerability in the company’s website that let them access the firm’s corporate network. From there, they used tools to encrypt the firm’s files – stopping the company from accessing them. Then the hackers started sending messages, demanding payment for the firm to gain access to its own files.
This type of attack, known as a ransomware attack, is a common tactic for cyber criminals looking to exploit security flaws and extort money. Within a four-month period this year, major contractors Bouygues UK, Bam and Interserve all fell victim to malicious actors targeting their systems. They were the first public high-profile cases of modern cyber attacks on major construction firms but, given the prevalence of technology in the industry, it is unlikely they will be the last.
Hill himself had arrived at Bam a couple of years earlier as part of the Dutch multinational’s efforts to shore up its online defence. He had previously worked at telecom business KCOM and immediately noticed the difference with construction.
“These were very serious professionals. They knew what they were doing. They were deploying some very sophisticated hacking tools. The Netwalker [ransomware tool] was custom modified specifically to target Bam”
“Coming to the construction industry was a bit like coming to The Wild West, “From a heavily regulated IT company within KCOM – where there were 2,000 employees, 1,500 [of whom were] in IT – it was a different world. At KCOM, if they didn’t make 30 per cent margin in a year, they thought that was disastrous.”
The telecommunications industry was, under “constant attack”, which would prove to be good experience for his move to construction. Fortunately for Bam Construct, Hill had recently been rolling out new defence systems for the company designed to flag suspicious activity – the kind of tools that can identify such a ransomware attack. The program he installed, Varonis, flagged that an attack was happening on 3 May this year, which prompted his colleague’s call in the early hours of 4 May. “These [attackers] were very serious professionals,” Hill says.
“They knew what they were doing. They were deploying some very sophisticated hacking tools with versions. The Netwalker [ransomware tool] was custom modified specifically to target Bam.” Despite the attack demanding money from the contractor on the surface, the way it was actually carried out – with a different method of payment being created for each encrypted file – would have made it fairly difficult for them to have paid a large ransom and for the attackers to collect the money themselves. This made Hill suspicious about the real motive behind the attack: “This wasn’t so much about the money; it was about causing as much disruption as possible.”
The company was able to contain the threat within 24 hours but kept some systems, including its website, offline for more than a week in order to check and analyse the impact on them. A spokesman says there was a minor effect on payment systems, but the company lost no money and investigations found no evidence of data loss; the threat was contained, and the contractor has since strengthened its cyber defences.
What was the motive?
But why was a £950m-turnover construction company subjected to an attack that was designed to cause maximum disruption rather than extort it for cash? Two days after the attack on Bam Construct started, the UK’s National Cyber Security Centre and US Department of Homeland Security jointly issued a statement warning that companies involved in national responses to COVID-19 were being increasingly targeted by cyber criminals. The statement did not name construction companies as being specifically at risk but, a month earlier, Bam Construct had worked on turning the Harrogate Convention Centre into a Nightingale hospital.
On 12 May, Interserve – which had delivered Birmingham’s Nightingale hospital in April – released a statement revealing that it had been hit by a cyber attack earlier in the month. At the time, it said it was working with law enforcement to remedy the situation and had informed the Information Commissioner of the incident – a step that must be taken if it is believed that data may have been compromised. The firm declined to be interviewed for this feature owing to the incident being “part of an ongoing criminal investigation”. A spokeswoman for the National Crime Agency, which is looking into the Interserve attack, says an investigation is ongoing and no arrests have been made.
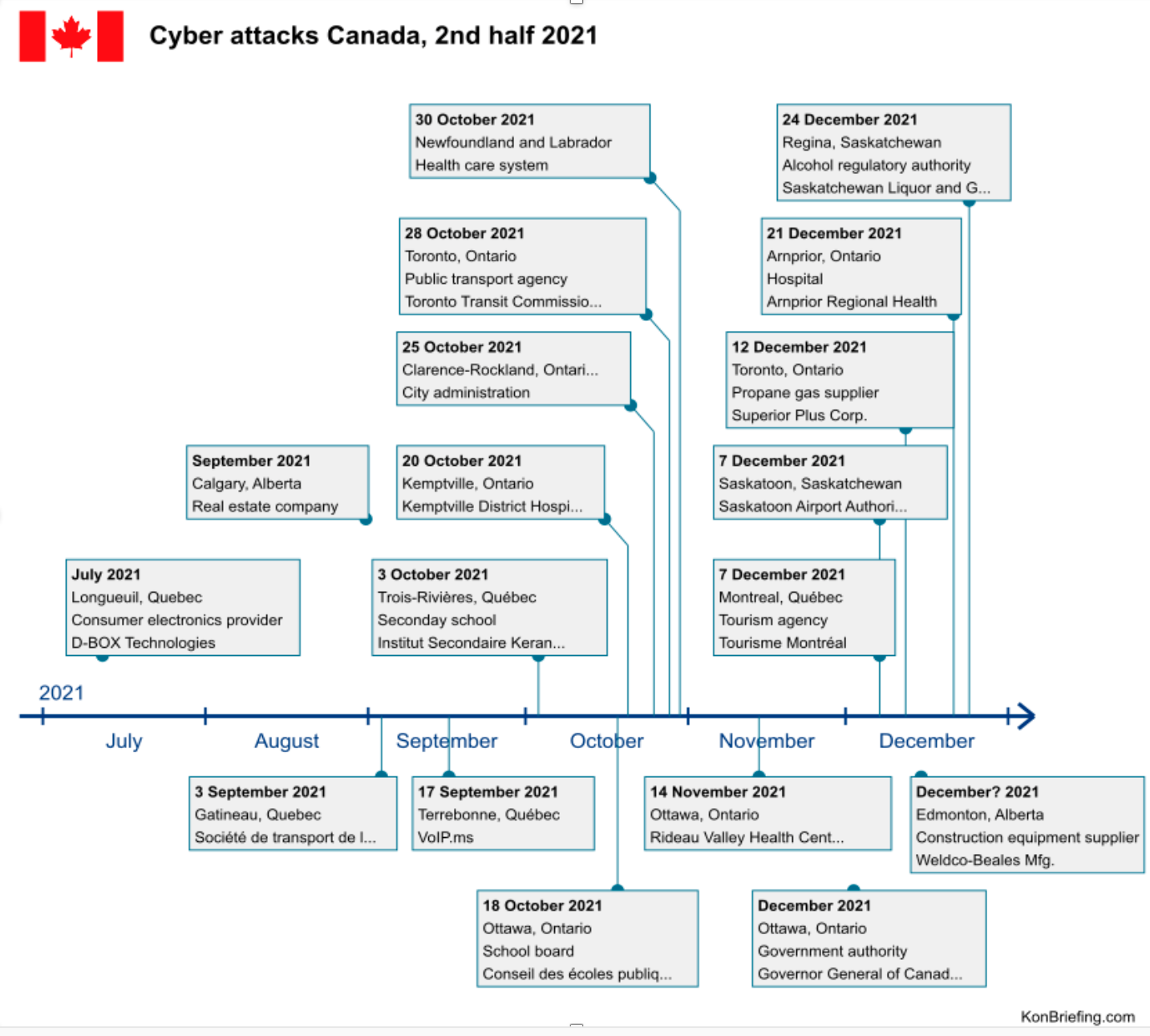
Cyber-attacks Known to affect the Canadian Government in 2022.
October 12, 2022
Cyberattack on Canadian government systems
Ottawa, Ontario, Canada
MPs warned to change email passwords after cyber attack on Canadian government
https://www.thestar.com/politics/federal…
September 14, 2022
Cyber attack on a city in Canada
Ville de Laval – Laval, Québec, Canada
Interruption des services infirmaries : la Ville fait un état de situation
https://www.laval.ca/Pages/Fr/Nouvelles/…
La Ville de Laval cable par une cyberhate
https://www.journaldemontreal.com/2022/0…
September 11, 2022
Cyber attack on a Canadian university
University of Guelph – Guelph, Ontario, Canada
U of G Student upset over lack of transparency after cyber breach
https://kitchener.ctvnews.ca/u-of-g-stud…
https://news.uoguelph.ca/systems-status/
September 8, 2022
Cyber attack on a regional government in Canada
Sunshine Coast Regional District (SCRD) – Sechelt, British Columbia, Canada
Recent Cyber Incident at the SCRD
https://www.scrd.ca/files/File/Administr…
August 23, 2022
Cyberattack on a non-profit care organization in Canada
St.Amant – Winnipeg, Manitoba, Canada
St. Amant Informing Stakeholders of Network Breach
https://stamant.ca/media-advisory-st-ama…
August 2022
Cyber attack on a telecommunications service provider in Canada
Bell Technical Solutions – Canada
Hive ransomware claims cyberattack on Bell Canada subsidiary
https://www.bleepingcomputer.com/news/se…
Bell Technical Solutions cybersecurity alert
https://www.bell.ca/Mobility/Bell-Techni…
August 8, 2022
Cyber attack on a vehicle manufacturer in Canada
BRP Inc. – Valcourt, Québec, Canada
https://news.brp.com/news-releases/news-…
August 7, 2022
Cyberattack on an agricultural union in Canada
L’Union des producteurs agricoles (UPA) – Longueuil, Quebec, Canada
L’UPA ciblée par une « cyberhate majeure » depuis dimanche
https://www.lapresse.ca/affaires/2022-08…
July 20, 2022
Cyber attack on a town in Ontario, Canada
St. Mary’s, Perth County, Ontario, Canada
Town of St. Mary’s investigating cyber security incident
https://www.townofstmarys.com/en/news/to…
July 10, 2022
Cyber attack on a school board in Ontario, Canada
Waterloo Region District School Board – Kitchener, Ontario, Canada
Data stolen during ‘cyber incidents’ at Waterloo Region District School Board
https://kitchener.ctvnews.ca/data-stolen..
June 20, 2022
Cyber attack on a university in Ontario, Canada
University of Windsor – Windsor, Ontario, Canada
UPDATE: Cyber attack blamed for computer outage at U of W
https://blackburnnews.com/windsor/windso…
June 8, 2022
Unauthorized access at an IT service provider for credit unions in Canada
Celero Solutions – Calgary, Alberta, Canada
https://www.cbc.ca/news/canada/manitoba/…
June 3, 2022
Cyberattack on the National Library of Québec, Canada
Bibliotheque et Archives nationals du Québec (BAnQ) – Montreal, Québec, Canada
Interruption prolonged des services en ligne de BAnQ
https://www.facebook.com/banqweb20/
May 31, 2022
Unauthorized access at a Canadian avionics manufacturer
CMC Electronic – Montreal, Québec, Canada
Canadian military provider suffered ransom attack, says news report
https://www.itworldcanada.com/article/ca…
May 22, 2022
Cyberattack on a school division in Regina, Canada
Regina Public School Division (RPSD) – Regina, Saskatchewan, Canada
Message from Regina Public Schools on Thursday, May 26, 2022
https://twitter.com/RegPublicSchool/stat…
May 2022
Ransomware at a Canadian air combat training company
Top Aces Inc. – Montreal, Québec, Canada
Canadian fighter jet training company investigating ransomware attack
https://therecord.media/top-aces-ransomw…
May 11, 2022
Cyberattack on a college in Canada
Collège Montmorency – Laval, Québec, Canada
Le Collège Montmorency victime d’une cyberattaque
https://www.lapresse.ca/actualites/2022-…
April 18, 2022
Canadian airline affected by cyber attack
Sunwing Airlines – Toronto, Ontario, Canada
According to the press, there was a cyber attack on an external IT service provider. Thousands of passengers are stuck.
Sunwing technical issue continues to disrupt travel plans for thousands of passengers
https://www.cbc.ca/news/business/sunwing…
March 31, 2022
Cyber attack on a county administration in Canada
Elgin County – St. Thomas, Ontario, Canada
Local municipality still struggling to recover from ‘cyber security incident’
https://www.thestar.com/news/canada/2022…
March 19, 2022
Cyber attack on the city of Banff, Canada
Town of Banff – Banff, Alberta, Canada
The town of Banff is located in the province of Alberta, 140 km west of Calgary and has just under 8000 inhabitants.
Town of Banff investigates cybersecurity attack
https://www.rmotoday.com/banff/town-of-b…
18 March 2022
Cyberattack on a government research organization in Canada
National Research Council of Canada (NRC) – Ottawa, Ontario, Canada
Canada’s National Research Council detects ‘cyber incident,’ investigation underway
https://www.ctvnews.ca/mobile/politics/c…
March 3, 2022
Cyber attack on a digital newspaper provider
Press Reader – Richmond, British Columbia, Canada
https://about.pressreader.com/
February 2022
Cyber attack on an aerospace manufacturer in Canada
IMP Group – Halifax, Nova Scotia, Canada
Halifax company that wants to assemble fighter jets comes under cyber-attack
https://www.saltwire.com/atlantic-canada…
February 25, 2022
Cyber attack on an aluminum manufacturing company in Canada
Aluminide Alouette – Sept-Îles, Québec, Canada
https://www.alouette.com/medias/nouvelle…
February 21, 2022
Cyber attack on a packaging manufacturer in Canada
Winpak – Winnipeg, Manitoba, Canada
Manufacturing firm Winpak brought to its knees by hackers
https://www.winnipegfreepress.com/local/…
February 2022
Ransomware at a technology company in Canada
Panasonic Canada Inc. – Mississauga, Ontario, Canada
Panasonic says Canadian operations hit by ‘targeted’ cyberattack
https://techcrunch.com/2022/04/11/panaso…
January 25, 2022
Unauthorized access at a healthcare provider in Ontario, Canada
Scarborough Health Network (SHN) – Toronto, Ontario, Canada
SHN Personal Information Public Notice
https://www.shn.ca/publicnotice/
January 19, 2022
Cyber attack on the Canadian Ministry of Foreign Affairs
Global Affairs Canada – Ottawa, Ontario, Canada
Global Affairs Canada hit by ‘cyber incident’ same day warning about Russia was issued
https://www.ctvnews.ca/politics/global-a…
January 2022 Ransomware at an art center in Canada Confederation Centre of the Arts – Charlottetown, Prince Edward Island, Canada
Investigation reveals thousands had info exposed in P.E.I. arts centre data breach
Only by going through the freedom of Information was the above cases made available, they almost never get into the media, which is an even bigger concern.
Bio:
Dr. Bill Pomfret of Safety Projects International Inc who has a training platform, said, “It’s important to clarify that deskless workers aren’t after any old training. Summoning teams to a white-walled room to digest endless slides no longer cuts it. Mobile learning is quickly becoming the most accessible way to get training out to those in the field or working remotely. For training to be a successful retention and recruitment tool, it needs to be an experience learner will enjoy and be in sync with today’s digital habits.”
Every relationship is a social contract between one or more people. Each person is responsible for the functioning of the team. In our society, the onus is on the leader. It is time that employees learnt to be responsible for their actions or inaction, as well. And this takes a leader to encourage them to work and behave at a higher level. Helping employees understand that they also need to be accountable, visible and communicate what’s going on.