On February 26, 2024, the National Institute of Standards and Technology (NIST) issued several Cyber-Security Frameworks. These included: a.) Cyber-security Framework 2.0 Small Business Quick-Start Guide, b.) Cyber-security Framework (CFS) 2.0 Resources Overview Guide, c.) Cyber-security Framework 2.0 Quick Start Guide, and Cybersecurity Framework 2.0: Enterprise Risk Management Quick-Start Guide. Another manual Enterprise Risk Management and Governance Oversight was issued on March 6, 2024. (1) These guides and manuals indicate the NIST is attempting to provide a wide range of information on cyber-security for different sectors of the economy, which have different levels of risk management sophistication.
On February 26, 2024, the National Institute of Standards and Technology (NIST) issued several Cyber-Security Frameworks. These included: a.) Cyber-security Framework 2.0 Small Business Quick-Start Guide, b.) Cyber-security Framework (CFS) 2.0 Resources Overview Guide, c.) Cyber-security Framework 2.0 Quick Start Guide, and Cybersecurity Framework 2.0: Enterprise Risk Management Quick-Start Guide. Another manual Enterprise Risk Management and Governance Oversight was issued on March 6, 2024. (1) These guides and manuals indicate the NIST is attempting to provide a wide range of information on cyber-security for different sectors of the economy, which have different levels of risk management sophistication.
The ultimate manual which the quick starts lead up to is CFS 2.0. Since I discussed the NIST CFS 2.0 public draft in CERM Risk Insight # 431, October 1, 2023, this article will look at the CFS 2.0 Resource & Overview Guide and the Enterprise Risk Management Quick-Start Guide.
The CFS 2.0 Resource & Overview Guide presents an overview of the CFS 2.0 and the resources available to assist in operationalizing the framework. The Enterprise Risk Management (ERM) Quick-Start Guide places the CFS 2.0 Framework within the overall organizational risk management context and integrates the two.
Resource & Overview Guide
CSF 2.0 is comprised of three sections. These are:
CFS Core – A taxonomy of high-level cybersecurity outcomes that can help any organization manage its cybersecurity risks. Taxonomy is a detailed listing of actions to consider under each of the CFS six functions. These functions are: Govern, Identify, Protect, Detect, Respond and Recover. These six functions operationalize CFS 2.0.
Each function is a broad activity statement. Under each function has under it a subset of actions to be taken. For instance, the Govern function includes the organization’s cybersecurity risk management strategy, expectations, and policies. One subset is to: Develop a tailored cybersecurity strategy. Another is to: Define risk management policies.
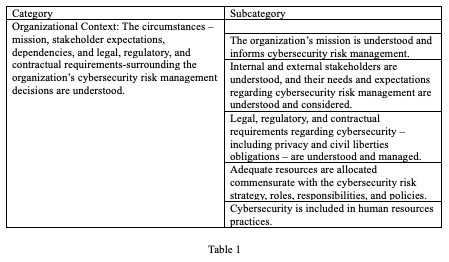
CFS Organizational Profile – A mechanism for describing the organization’s current cybersecurity status and the mitigative action taken to minimize the risks of a cyber-attack. Essentially, the profile is a cyber-security risk register. This risk register can be integrated into the organization’s overall ERM risk register. Table 1 below shows an example of the profile.
CSF Tiers – These can be applied to the CSF Organizational Profiles to characterize the rigor of the organization’s cybersecurity risk governance and management practices.
There are four tiers. These are Partial, Risk Informed, Repeatable, and Adaptive. Each represents a level of cybersecurity risk management sophistication. The Risk Informed level is described as:
- There is an awareness of cybersecurity risks at the organizational level, but an organization wide approach to managing cybersecurity risks has not been established.
- Cybersecurity information is shared within the organization on an informal basis.
- The organization is aware of the cybersecurity risks associated with its suppliers and the products and services it acquires and uses but does not act consistently or formally in response to those risks.
To move to Repeatable or Adaptive the organization would have to have an organization wide approach to mitigate cybersecurity risks and have a formal and consistently acted upon cybersecurity risk management plan for suppliers, to mention two of the actions the organization must take. Each rise in level requires more sophisticated and comprehensive risk management activities.
Some of the resources provided include Concept papers, Frequently Asked Questions and a Community Profile template.
Enterprise Risk Management Quick Start Guide
The CFS ERM Quick Start Guide is specifically developed to assist with the planning and integration of cybersecurity risk management information into the organization’s ERM process. NIST, with this guide, recognizes that cybersecurity is a subset of Information Communication and Technology, which in turn is a subset of the enterprise operation.
NIST believes that CFS 2.0 as “part of a holistic ERM approach, helps ensure that leaders continually have information they need for making informed business/agency decisions.”
To help with this integration process NSIT emphasizes six activity points. These are:
- Leaders define and record enterprise mission, priorities, and risk appetite. They assign accountability for managing both positive and negative risks.
- Organization – level- managers interpret risk appetite into specific guidance regarding security and privacy requirements, and associate risk tolerance.
- Risk strategy and requirement aid implementation of shared security solutions and system level controls to achieve acceptable risk levels.
- Risk response outcomes are reflected as residual risks in system level risk registers as part of ongoing assessment and continuous monitoring activities.
- Risk registers are normalized and aggregated at the organizational unit level, supporting reporting, analysis, and organizational-level adjustments.
- Combined risk results from the enterprise are used to maintain an enterprise-level risk register and risk profile.
The six activity points encapsulate the ERM process at the organizational level. At the operational level – cybersecurity – CFS 2.0 stresses a cycle of continual monitoring and adjustment, consistent with the risk tolerance and organization’s objectives. (This monitoring cycle is like that presented in ISO 31000:2018 and COSO-ERM.) It consists of three steps, with several actions under each step. The steps and actions are below.
Monitor
- Measure whether controls are still implemented and effective.
- Measure the extent to which controls are implemented without impairing organizational operations and efficiency.
Evaluate
- Assess if organizational controls are achieving the desired risk results.
- Assess if risk management activities are keeping risk within tolerance of risk appetite.
Adjust
- Implement additional controls and enhancement as needed.
- Implement alternative controls to enhance opportunity.
The evaluation process is one of continual monitoring the organization’s risk registers. The registers, as noted in the CFS 2.0 Resource & Overview Guide, are the “community profile”. This profile expresses the level of risk management sophistication. The monitoring helps determine the effectiveness of the mitigation efforts for each risk identified on the risk register and thus the organization’s risk management success. Where adjustments need to be made, either because the risk has been mitigated, in which case it might be eliminated from the register, or additional mitigative actions needs to be taken, because the efforts have not been as effective as desired, or the risk tolerance has changed, they are made.
Conclusion
The issuance of multiple quick start guides by NSIT is recognition of the complexity of the U.S. economy and the diversity in risk management sophistication. This recognition is reflected in the CFS 2.0 quick start for Small Business, as well as the quick starts for CFS 2:0 and ERM.
The quick start provides the reader with the basics and eases into the process of Risk Based Thinking. That is thinking about the risks their organization faces and how to mitigate those risks, be they cybersecurity or other operational risks. From the quick starts the reader can move to the full CSF 2.0 or Enterprise Risk Management and Governance Oversight manuals.
It cannot be emphasized enough that cybersecurity is a subset of Information Communication and Technology, which in turn is a subset of the enterprise’s operations. The computer, networks, and the Internet of Things, are so entwined into the most organizational day-to-day operations, as to be inseparable. Thus, CFS 2.0 needs to be seen as an integral component of the organization’s ERM process.
Endnotes
- National Institute of Standards and Technology, 2024, Special Publications, https://www.nist.gov/publications/search?ta%5B0%5D=248731 All publications listed.
James J. Kline, Ph.D., CERM. He has worked in federal, state, and local government. He has authored numerous articles on quality in government and risk management. His two books Enterprise Risk Management in Government: Implementing ISO 31000:2018 and Risk Based Thinking for Government are available on Amazon. Also available on Amazon is Quality Disrupted, which he edited. He can be reached at jamesjk1236@outlook.com.