 In my last article “Is Cloud based Risk Management worth the Risk?” I confirmed cloud solutions can be the right and effective solution given that you do the appropriate due diligence on being fit-for-purpose. If a cloud solution is appropriate, that’s any application not just risk and compliance, then how can you minimise your internet infrastructure risk?
In my last article “Is Cloud based Risk Management worth the Risk?” I confirmed cloud solutions can be the right and effective solution given that you do the appropriate due diligence on being fit-for-purpose. If a cloud solution is appropriate, that’s any application not just risk and compliance, then how can you minimise your internet infrastructure risk?
With over 16 years’ experience working in security conscience environments at Dept of Defence, Victorian Infectious Disease Ref Labs, and Australian Border Security, I have put together my top 10 suggestions for mimimizing your risks when moving to cloud computing.
1. Get a professional IT threat assessment
If you have ascertained the cost-benefit of using a cloud solution then have your gut feel backed up by an expert. They will also offer advice on mitigating a range of risks you may not even have thought of. Just make sure you use an accredited IT security consultant, such as Certified Information Systems Security Professional (CISSP), not a generalist management consultant. It is such a fast changing field you need a true specialist.
 2. Use a major multi data centre hosting provider
2. Use a major multi data centre hosting provider
Go with a major hosting provider, avoiding backyard providers and software providers hosting their own solutions. Firstly, economies of scale in cloud hosting will see a lot of the small players fall by the wayside in the next few years. If your cloud provider’s business fails, at best you will have outages and migration costs, at worst you could lose access to even your data. Secondly, with major providers security of data in the cloud is not an issue. Outside data sovereignty issues, their physical, environmental, and data security will most likely outrank all but Dept. of Defence security.
3. Set up multiple domain coverage
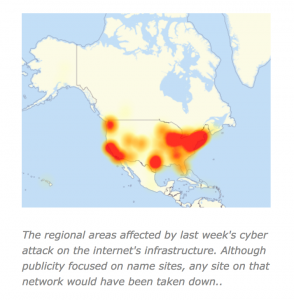
Internet infrastructure is managed around domains like .com.au and .co.uk. These are the gateways targeted in last week’s attack. By having alternative backup domains managed in separate regions you may be still be able to access your sites using different URLs.
4. Select a hosting provider with cross geographic fail-over
Having your sites continually automatically backed up to another physical data centre (separated by over 100 miles) is a common option available thru the major hosting providers at a small additional cost. This adds a level of protection (yes at a cost) against physical infrastructure (power, weather, telecom failure, etc.) disruption. Basis disaster recovery is normally only provided at the same physical location.
5. Encrypt your data in the cloud
Data encryption is where data cannot be understood without a special decryption key that is only available in your application(s). Encryption can be instigated both “at rest” (where it is stored in the cloud) and/or “in transit” (while being delivered to a user’s PC or mobile device). Both are targets for hackers or journalists. That means even if someone does hack your cloud provider, or the public network, they only see garbage. The level of encryption made available by major hosting providers is Dept. of Defence grade and basically unbreakable.
6. Use Multi Factor Authentication for user access
Most people have heard the expression “defence in depth”. This is because if you use multiple security gates to access your system, hackers can’t run their hacking tools between the security gates. A simple but very effective strategy, although not widely used. Multi Factor Authentication (or MFA) most commonly involves having the hosting provider text (SMS) a verification code back to the user’s phone after logging on to the network with a basic UserID and password, but before access is granted. The other common from is using a token held be the user which is synchronized with the hosting provider.
7. Investigate hybrid solutions where data is stored in-house
Hybrid solutions are where you use cloud provided software that accesses the data stored on your in-house server. Yes, this means maintaining your own internal infrastructure thereby negating a major part of the cost saving but does allow you to access state-of-the-art software but still have control over your data.
8. Set up as a Virtual Private Network using IPSec
This requires more in-house IT expertise to set up and manage where only specified computers are given access to you system. This has the advantage of by-passing some of the global infrastructure gateways affected in last week’s attacks.
9. Use a Cloud Mitigation Provider as a defencive front-end
Cloud mitigation providers are additional cloud service providers that you go via to access your application provider(s). They are experts at providing DDoS mitigation from the cloud. This means they have built out massive amounts of network bandwidth and DDoS mitigation capacity at multiple sites around the Internet that can take in any type of network traffic, whether you use multiple ISP’s, have your own data centre, or any number of cloud providers. They can scrub the traffic for you and only send “clean” traffic to your data centre.
10. Your biggest threat is your own staff
This is not meant to be a comprehensive cloud security playbook, but just some simple steps you can undertake that would deter/defeat all but the professional (state based) cyber-attacks. But also be aware that your greatest security risk is your own users. Ex-employees, staff with a grudge, or even poorly trained staff can result in unsophisticated loss, corruptions, or release of data more often than 3rd party attacks. With security there is no substitute for proper training, staff awareness and vigilance in staff attitudes.
Bio:
Greg Carroll - Founder & Technical Director, Fast Track Australia Pty Ltd. Greg Carroll has 30 years’ experience addressing risk management systems in life-and-death environments like the Australian Department of Defence and the Victorian Infectious Diseases Laboratories among others. He has also worked for decades with top tier multinationals like Motorola, Fosters and Serco.
In 1981 he founded Fast Track (www.fasttrack365.com) which specialises in regulatory compliance and enterprise risk management for medium and large organisations. The company deploys enterprise-wide solutions for Quality, Risk, Environmental, OHS, Supplier, and Innovation Management.
Mastering 21st Century Risk Management” which will be available from the www.fasttrack365.com website in a couple of weeks. Meanwhile a recent Webinar on the topic can be seen at http://www.youtube.com/watch?v=nQoJj6FBxrY&feature=youtu.be in which we show how emerging best practices provide a good picture for how enterprise risk management should look in the 21st century.