On August 8, 2023, the National Institute of Standards and Technology (NIST) issued an Initial Public Draft of The NIST Cybersecurity Framework 2.0. (1) This framework issued for public comment and review, updates Framework for Improving Critical Infrastructure Cybersecurity.
On August 8, 2023, the National Institute of Standards and Technology (NIST) issued an Initial Public Draft of The NIST Cybersecurity Framework 2.0. (1) This framework issued for public comment and review, updates Framework for Improving Critical Infrastructure Cybersecurity.
The primary audience for Framework 2.0 is those responsible for developing and leading a cybersecurity program. However, the framework can also be used by anyone involved in risk management such as executives, boards of directors, technology professionals, risk managers, lawyers, and cyber security and risk management auditors. This is because the framework has been designed so it can be used by anyone in any type of organization.
Except for federal agencies, the application of Framework 2.0 is voluntary. However, any organization which contracts with a federal agency, will likely be required to demonstrate compliance with the framework.
Overview
Broadly speaking Framework 2.0 provides the organization with a structure that allows it to understand, assess, prioritize, and communicate cybersecurity risks. These general categories provide the basic Framework 2.0 structure. For instance, under Understand and Asses, management is encouraged to:
- Describe the current or target cybersecurity posture within and across all aspects of the organization be it department, or business unit.
- Determine where there are cybersecurity gaps, existing or emerging threats or technologies and assess actions taken address these gaps.
- Align policies, procedures, and technology to management cybersecurity risks.
A key goal under Prioritize is:
- Identify, organize, and prioritize actions for reducing cybersecurity risks that align with the organization’s mission, legal and regulatory requirements, and risk management and governance expectations.
A key goal under Communicate is:
- Complement an organization’s risk management process by presenting a concise way for executives and others to distill the fundamental concepts of cybersecurity risk for them to understand its importance and how their organization manages these risks.
These broad categories indicate that NIST’s goal is not only to provide a framework which will improve cybersecurity but encourage Framework 2.0’s integration into the organization’s overall risk management process. This can be seen in Understand and Assess where it is emphasized that cybersecurity should be understood as crossing functional activity lines. Similarly, Under Prioritize and Communicate, there is an emphasis on the integration of cybersecurity risk management with an enterprise-wide risk management process.
The broad categories are supported by a structure which contains six functional areas. The functional areas are further divided into categories and subcategories.
Basic Structure
The six key functional areas are:
- Govern – establish and monitor the organization’s cybersecurity risk management strategy, expectations, and policy.
- Identify – help determine the current cybersecurity risk to the organization.
- Protect – use safeguards to prevent or reduce cybersecurity risk.
- Detect – find and analyze possible cybersecurity attacks and compromises.
- Respond – act regarding a detected cybersecurity incident.
- Recover – restore assets and operations that were impacted by a cybersecurity incident.
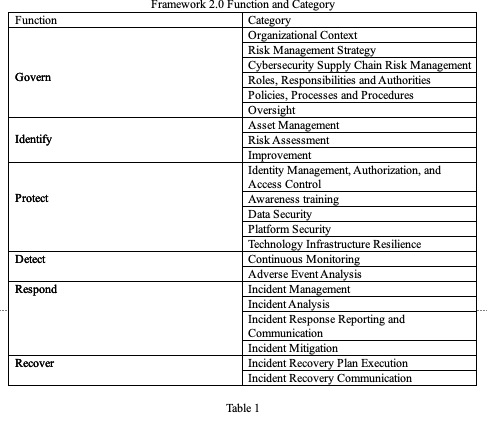
Govern is a new category added to Frame 2.0. Table 1 below shows the functional areas and the associated categories.
Of the categories, Cybersecurity Supply Chain Risk Management is emphasized in Framework 2.0, as opposed to the first Cybersecurity framework. (Both Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations (SP800-55) and the integration of Cybersecurity with ERM have separate guides (NIST IR 8286). NIST has add a section on the integration of Cybersecurity into the organization’s ERM process to Framework 2.0.)
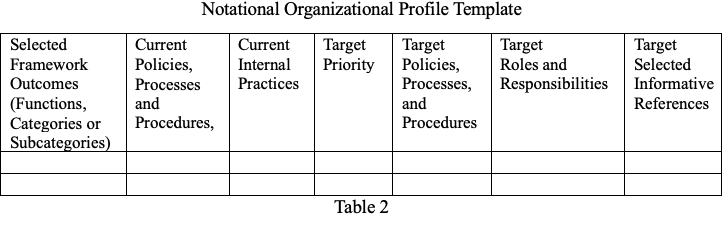
To facilitate communication and risk management identification and assessment, Framework 2.0 provides a Notational Organizational Profile Template. The template structure can be used to help identify and analyze cybersecurity risks. It can also be used more broadly to analyze all organizational risks by merely changing the functions or subcategories used. Table 2 shows the basic template.
As can be seen, the template walks the user through different aspects of risk analysis and assessment. The end results are the identification of associated risks and the development of mitigative actions, the assignment of mitigation implementation and responsibilities.
Conclusion
NIST has updated its Cybersecurity Risk Management framework. It has added Govern to its key functional areas. It has also emphasized Supply Chain Cybersecurity and the integration of the framework into the organization’s ERM process.
While the use of Framework 2.0 is a requirement for United States (U.S.) federal agencies, it is designed to be used by any organization regardless of economic sector and size. Further, if an organization works or contracts with U.S. federal agencies, compliance with Framework 2.0 is likely to be required.
Finally, while Framework 2.0 is an initial draft, and open for comment, it is doubtful the basic structure or emphasis will change. Consequently, given the concern for cybersecurity, and the general applicability of the framework, its use will probably extend beyond federal agencies and those who work or contract with the federal government.
Endnotes
- National Institute of Standards and Technology, 2023, The NIST Cybersecurity Framework 2.0 Initial Public Draft, August 8, https://nulpubs.nist.gov/nistpubs/cswp/nist.cswp.29.ipd.pdf
BIO
James J. Kline has worked for federal, state, and local government. He has over ten year’s supervisory and managerial experience in both the public and private sector. He has consulted on economic, quality and workforce development issues for state and local governments. He has authored numerous articles on quality and risk management. His book “Enterprise Risk Management in Government: Implementing ISO 31000:2018” is available on Amazon. He is the editor of “Quality Disrupted’ which is available on Amazon.