 Risk based decision making is employed to implement risk management. But how is this implemented? In this article we will look at the process of making “risk based” decisions.
Risk based decision making is employed to implement risk management. But how is this implemented? In this article we will look at the process of making “risk based” decisions.
Risk management is a process that involves several activities.
- Risk Assessment, to identify and assess risks and Risk Events;
- Ranking or prioritizing the most significant or critical risks;
- Risk-based Decision Making, to determine mitigations or defensive actions for the critical risks;
- Monitoring the risk environment for changes in the risk rankings or for new risks; and
- Periodically updating the risk assessments, priorities, and mitigations.
The elements of Risk-based decision making are:
- A Risk Assessment Process,
- Determination of risk event Likelihood/Probability (qualitative/quantitative) and Consequence,
- Risk Characteristics and Factors such as Onset and Duration,
- A Risk Representation mechanism (Risk Matrix or Heat Map),
- Risk Decisions (Prioritization, mitigation/treatment).
Risk Assessment Process. This process is customarily associated with a Risk Management Framework. Depending on your country, industry and other factors there are several options: ISO 31000[1] (the international standard), COSO[2] (developed for finance and now operations), NIST RMF[3](Federal IT).
Each Risk Framework defines what a risk is and describes a process flow for defining, assessing and managing risks. While there are differences in terminology, and variations in details in how the various steps are performed, they all are basically describing the same process. COSO defines risk as an event that adversely affects the ability of the organization to achieve objectives. ISO defines risk as the effect of uncertainty on objectives. The IIA (Institute of Internal Auditors) defines risk as “the possibility of an event occurring that will have an impact on the achievement of objectives”. Risk is generally described in terms of the likelihood (or possibility) and the consequence of its occurrence on some objective. Objectives are described in terms of the organization’s business strategy and goals.
Risk Assessment involves Risk Identification and Determination of the importance of the resulting risks. Risk Identification is the process of identifying risks and the events that could occur related to the risks. This can be accomplished by generating a list of risk events by brainstorming the answers to the general question “what could happen”. Or for each business objective, analyzing and asking “what could affect its achievement”, creating a focused list of risk events.
Determination of Likelihood/Probability and Consequence. Each risk and risk event is assessed, and assigned a probability (aka likelihood) for its occurrence and an evaluation of the resulting consequences. The likelihood and consequences of the risk can be determined in a quantitative or qualitative manner. In many cases assigning a quantitative value is difficult and using a qualitative scale, such as 1-5 (with 1 being ‘low’ and 5 ‘high’) is the most reasonable approach. People are notoriously bad when assessing probabilities (e.g. what is 25% vs 33%), so discrete steps are easier to use. If there is data available from past history, or metrics associated with the risk consequences, then that can be used to provide a more accurate quantitative estimate than a qualitative measure. For example, if a consequence is that some process which produces $X worth of value per hour will be out of order, and the severity can be expressed in hours, then a numerical cost can be assigned to each degree of severity for the consequence (e.g., negligible, $X, $2X, $5X $10X etc.).
Risk Characteristics. Risk events may have characteristic factors or attributes that modify aspects of the event likelihood or its consequences. The factors can be defined in terms of the subject area of the risk, e.g. IT vs finance vs marketing. For example, Deloitte has a white paper, ‘Risk Assessment in Practice’[4], and the OWASP publishes a ‘Risk Rating Methodology’[5] guide on IT web application risks.
Risk Representation. Once the risks and risk events have been determined, they need to be represented and presented. This can be accomplished in either a textual or pictorial manner. The text form is commonly called a Risk register. The pictorial form is called a risk heat map or risk matrix.
After determining the likelihood and consequences, the risks are prioritized (ranked). The likelihood and consequence values are multiplied to create a scoring value. The score is then plotted on the heat map or recorded in the risk register. The risk appetite and /or risk tolerance of the organization is used to select which risks exceed the tolerance and thus need to be addressed and mitigated (reduced in likelihood and/or consequence).
An example risk heat map is shown below. There are three map areas indicating how ‘hot’ each risk is:
| Green | Low risk. This is in the lower left hand corner of the chart. |
| Yellow | Medium risk. This is in the middle of the chart. |
| Red | High risk. This is in the upper right hand corner of the chart. |
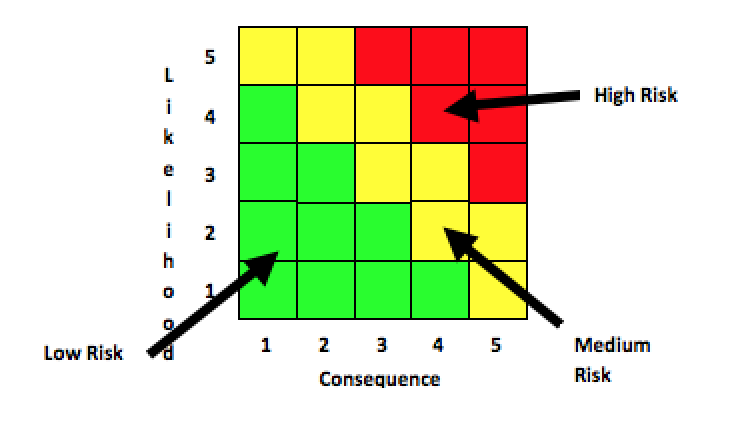 The highest ranked risks are analyzed to determine what actions can or should be taken to reduce their score below the risk tolerance. Once the risks have been prioritized, they can be recorded in a workbook or spreadsheet listing (aka “risk register”)
The highest ranked risks are analyzed to determine what actions can or should be taken to reduce their score below the risk tolerance. Once the risks have been prioritized, they can be recorded in a workbook or spreadsheet listing (aka “risk register”)
Risk-based Decisions. The process of identifying and ranking risks, to determine which are critical and above the organization’s risk tolerance or threshold and thus require attention, and then to select the risk management action(s) to take in response. Making risk-based decision(s) on which risk management actions to implement for each of the prioritized risks are:
- Avoid the risk – stop the risky activity or do not undertake the risky activity,
- Accept the risk – do not implement any mitigation(s),
- Share the risk – also referred to as transferring the risk – outsource the risky activity, obtain insurance to cover costs of risk event consequence(s),
- Mitigate the risk – also referred to as treating or reducing the risk – determine actions to take that reduce either the likelihood of the occurrence of the risk or the magnitude of the consequences of the occurrence.
The goal of mitigating the risk is to move its likelihood or consequence “down” the scale from the ‘red zone’ into the yellow or green zones. E.g . lower the likelihood or reduce the consequence. There might be multiple options for mitigation and they each need to be assessed to determine their effectiveness. While the risk likelihood may be reduced, the consequence may still be above the organizational risk tolerance or appetite.
Once a decision on mitigation or sharing a risk is made, the new likelihood and consequence needs to be reevaluated to determine if the modified risk in within the risk tolerance.
References
[1] ISO 31000, http://www.iso.org/iso/home/standards/iso31000.htm
[2] COSO, www.coso.org
[3] NIST RMF is specified in NIST special publications SP800-30 and SP800-39.
http://csrc.nist.gov/publications/PubsSPs.html
[4] ERM Risk Assessment in Practice (2012)
http://www.coso.org/documents/COSOAnncsOnlineSurvy2GainInpt4Updt2IntrnlCntrlIntgratdFrmwrk%20-%20for%20merge_files/COSO-ERM%20Risk%20Assessment%20inPractice%20Thought%20Paper%20OCtober%202012.pdf
[5] Open Web Application Security Project (OWASP) Risk Rating Methodology, https://www.owasp.org/index.php/OWASP_Risk_Rating_Methodology
Bio:
Ed Perkins CERM CIA is a risk management expert. He is the leader of CERM Cyber initiative as well as other national cyber security activities. He led the launch of the IEEE USA risk management webinar series. Ed has a number of counter intuitive ideas that we believe all engineers should hear. Ed believes that risk management is the fundamental career skill that all engineers must have. He goes a step further and believes that all engineers will evolve to be risk managers in today’s disruptive and uncertain times.
He can be reached at: EdP@QualityPlusEngineering.com