Tag Archives: Naresh Rao
#406 – DEMYSTIFYING ROLE OF IT IN BUSINESS CONTINUITY – NARESH RAO
Featured
#192 – ISO 31000 RISK VALIDATION – NARESH RAO
Featured
 ISO 31000 Says in “Introduction”
ISO 31000 Says in “Introduction”
Organizations of all types and sizes face internal and external factors and influences that make it uncertain whether and when they will achieve their objectives. The effect this uncertainly has an organization’s objectives is “risks”.
All activities of an organization involve risk. Organizations manage risk by identifying it, analysing it and then evaluating whether the risk should be modified by risk treatment in order to satisfy their risk criteria. Throughout this process, they communicate and consult with stakeholders and monitor and review the risk and the controls that are modifying the risk in order to ensure that no further risk treatment is required.
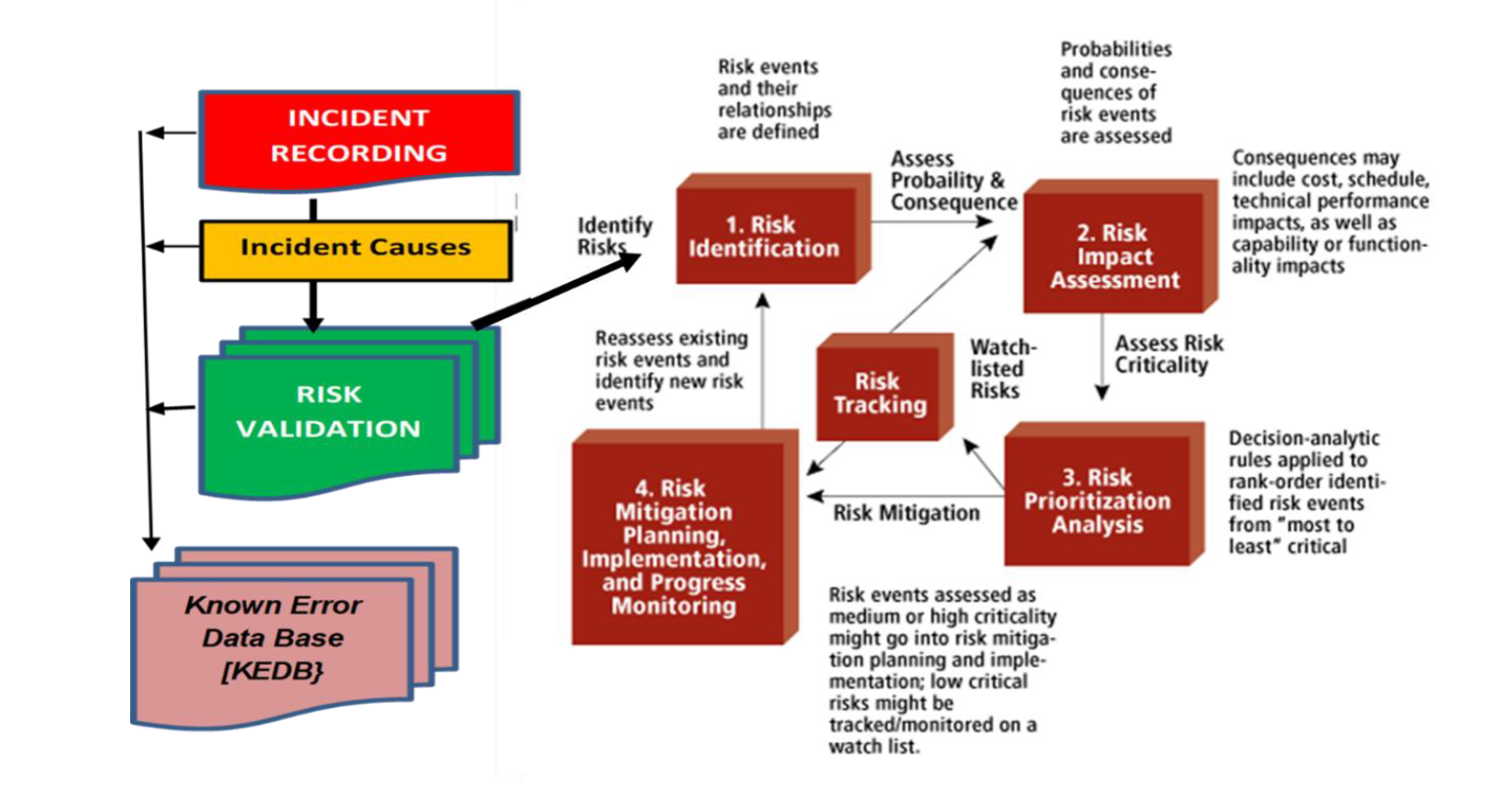
Risk Framework – Life Cycle with Risk Validation
The risks which are identified are based on what one’s vision can point out. There are many unearthed risks which “Risk Owner” may not be able to visualize and also may not be able to identify certain unknown risks or vulnerabilities, which may cause an incident.
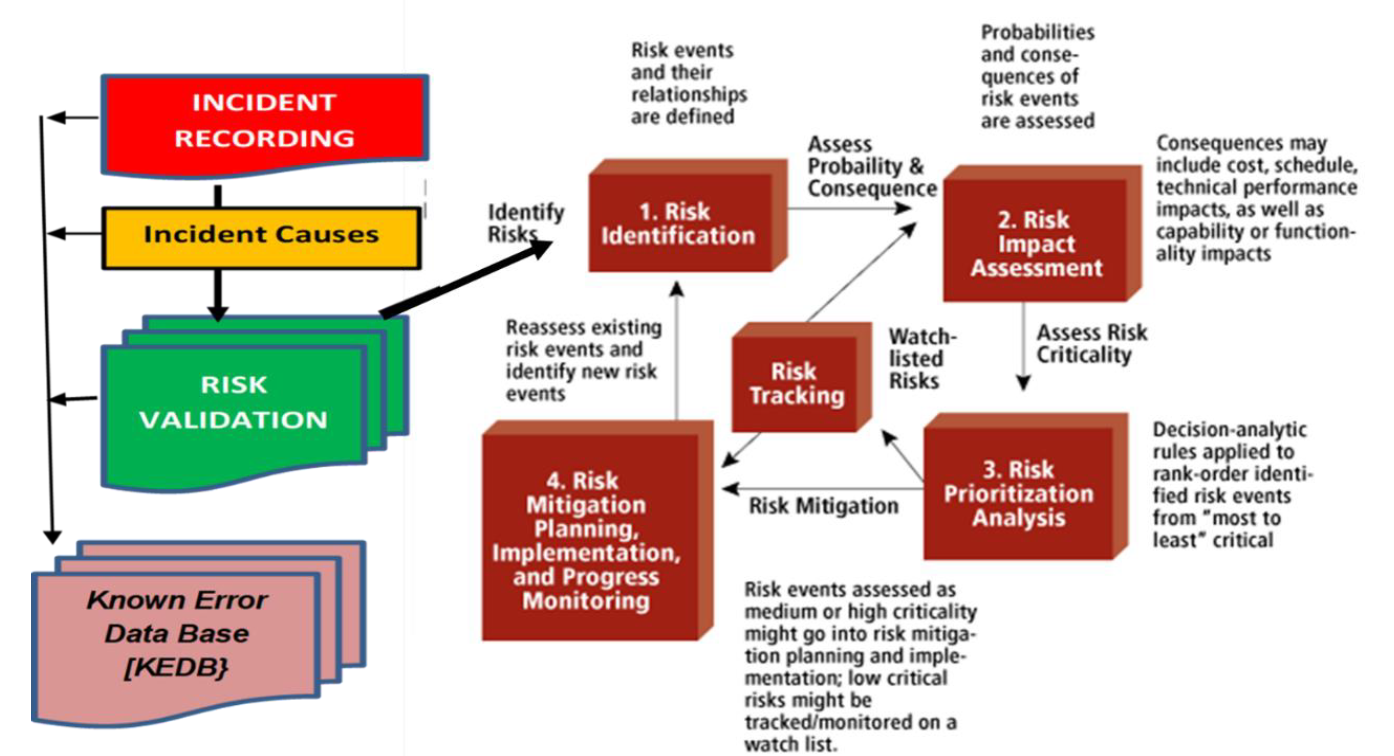
 The initial “Risk Identification” is done by the Risk Owners” based on:
The initial “Risk Identification” is done by the Risk Owners” based on:
➢ Past Experience
(Every Experience has a price to pay)
&
➢ Future Vision
 (Based on Capability and Capacity of the “Risk Owner”)
(Based on Capability and Capacity of the “Risk Owner”)
This means the Risk Management is Vision Based, initially.
Objective > How to convert Vision Based Risk Assessment to Factual Based Risk Assessment?
Why ?
Well > Evidence Based to Decision Making is the basic Principle of Management System and Auditing
Risk Evaluation
Before proceeding
to understand Risk Validation, it is important to look more deep into RISK MANAGEMENT:
- a) Risk Evaluation : Generally parameters considered in evaluating Risk are:
PROBABILITY OF OCCURANCE & SEVERITY OF IMPACT which consolidated result is considered as RISK LEVEL – this Risk Level can be achieved through Quantitative or Qualitative Methodology.
If you observe carefully following conclusion of Impacts differ between scenarios of Stable Asset or Moving Assets:
In Stable Assets – Probability Changes more than Severity
In Moving Assets – Severity of Impact Changes more than Probability
Examples >
STABLE ASSETS
MOVABLE ASSETS
In Industry, most of the processes work on IT platform and IT (Information Technology) falls under Stable Assets – thus any controls implemented (to reduce the risk), reduces the Probability – example is Firewall on Servers – all controls reduce the probability only as if they are breached, Impact is same – high risk.
Impact changing generally occur in Moving Assets like moving machine, health & safety like road accident (as shown above) or person falling from height (impact changes based on speed or height).
Risk Mitigation Effectiveness
- A) – Residual Risk Existence
Another important aspect of Risk Management is Control to reduce the risk – no matter what controls are put, the Risk Cannot be reduced to Zero – some element of residual risk is bound to be there.
The type of investment in mitigations depends on below or any combination
➢ Probability and / or Impact of vulnerability;
➢ Risk Appetite & Risk Tolerance;
➢ Monitoring Controls or Risk Reduction controls;
➢ Management perception of the Risk;
➢ Risk Owner’s perception of the Risk;
➢ Market influence on business;
➢ Competition perception;
➢ Risk Acceptance Criteria
The residual risk visualization / perception also gives rise to Risk Owner’s decision, in case Residual Risks are not acceptable.
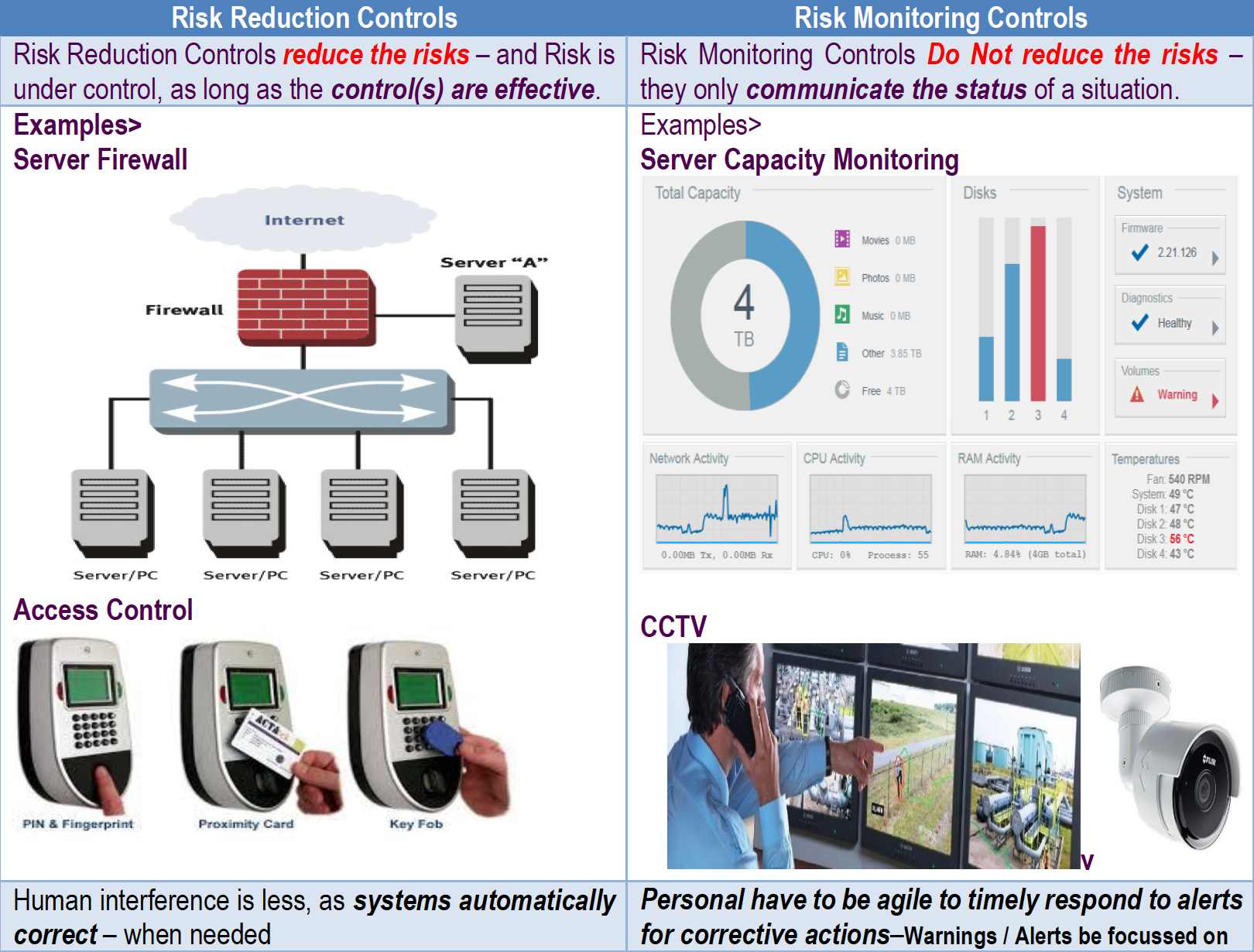
B) – Risk Control Effectiveness
There are two types of controls which exists
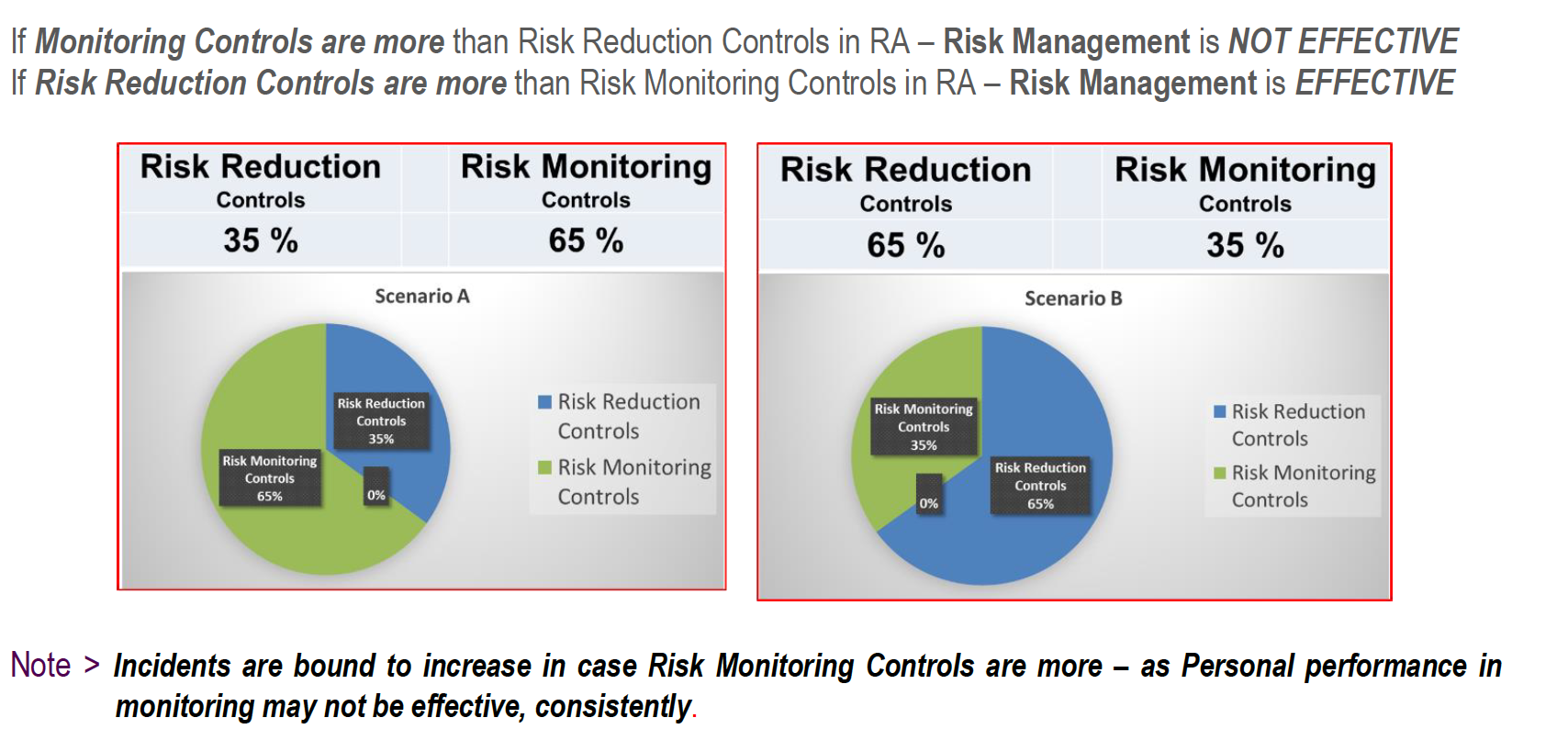
If Monitoring Controls are more than Risk Reduction Controls in RA – Risk Management is NOT EFFECTIVE
If Risk Reduction Controls are more than Risk Monitoring Controls in RA – Risk Management is EFFECTIVE
After all risks are identified, mitigated & monitored – what next?
Well, there is one more objective left out, which we discussed above:
Question>
– How to covert a vision based Risk Assessment into Factual based Risk Assessment?
Answer>
– Updating Risk Assessment after an incident occurs
Now “Risk Owners” have to do is – “Risk Validation” when incident happens
1) Identify the causes of the risks
2) Compare the causes of the incident to risk assessment and update the same – which is Risk Validation.
Some cautions are to be taken as below:
> Residual Risks
> Controls – Risk Reduction controls like (Server Firewall, etc.) and Monitoring Controls (like CCTV, etc.)
> Relevant Interested party not identified
> Interested party identified but not the risk or vulnerability
We need to know why the Incident occurred on first place, in spite of existing controls. Risk Validation shall help us to understand –which vulnerability in the Risk Assessment lead to the incident:
– The Risk Management Strategy OR
– Risk Process (criteria or evaluation or mitigation or acceptance criteria)
KEDB (Known Error Data Base) – updated after every Risk Validation in Incidents, apart from linking up to RA for required corrective actions. This updated KEDB is used for future reference, thus building up the knowledge base for the scope of the organization. By doing this, you are actually validating actual incidents with vision based current risks – thus converting vision based RA to Factual based RA.
Risk Assessment – Preventive Action Vs Corrective Action
As per Annex SL on which most of ISO Management Standards, new versions are released, the Preventive Action word is replaced by “Risk & Opportunities” there is no need for Preventive Actions;
– but when Risk Assessment is updated based on an incident – entire information of that specific risk (including controls & residual risks) now gets converted as corrective action(s) and do not remain as preventive, any more.
The definition of Corrective Actions is “Eliminating the causes of detected non-compliance and Pre-venting from recurrence”
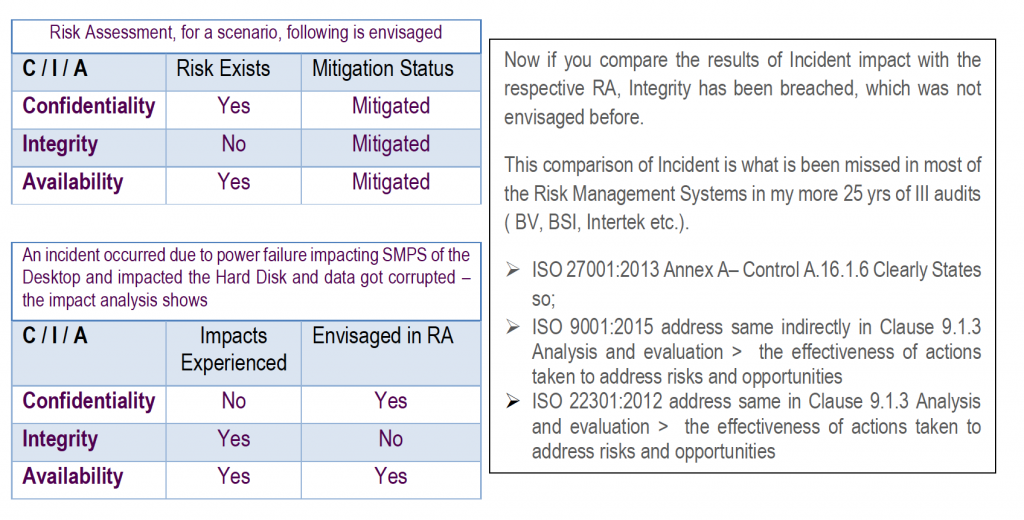
Example: (Information Security)
There are three parameters of Information Security:
➢ Confidentiality ( Information is available only to authorised personnel and not to unauthorized personnel )
➢ Integrity ( Accuracy and Completeness of Information )
➢ Availability ( Information is available to authorised personnel, when required)
Note >
If Confidentiality Breaches, changes of Integrity & Availability breaches automatically increases
If Integrity Breaches, chances of Availability breaches automatically increases
If Availability Breaches, then no risk for Confidentiality & Integrity is not there
Hope you have gained from this white paper on RISK VALIDATION and hope that this would benefit, if practiced. Requesting you to share your comments via mail to naresh@ircbo.solutions
Best Regards > Naresh RAO, Technical Director, IRCBO Solutions Pvt. Ltd., INDIA
Bio:
Started carrier from banking software development in 1986 then was an entrepreneur of textile mill. Entered Management Systems in 1993. Became and auditor with DNV(III CB) and later AQSR, RINA , KPMG, BSI and Intertek in senior positions like Regional Manager, Head Operations, General Manager , Head Standards and Business Solutions. Also a Lead Trainer in qualifying III party auditors on risk based standards. Now running a consulting firm in all Management system standards, apart from III party auditor for Intertek etc. and also has his own Lead Auditor course in Business Continuity (ISO 22301:2012) , Annex A based ISMS software (ISO 27001:2013 – new product about to be released globally)”
Naresh RAO,
Technical Director,
IRCBO Solutions Pvt Ltd.,
www.ircbo.solutions
mail > naresh@ircbo.solutions
mobile > +91 981182 7758