The Law Dictionary defines Collateral Risk as:
The RISK of loss arising from errors in the nature, quantity, pricing, or characteristics of COLLATERAL securing a transaction with CREDIT RISK. Institutions that actively accept and deliver collateral and are unable to manage the process accurately are susceptible to loss. A subcategory of PROCESS RISK.
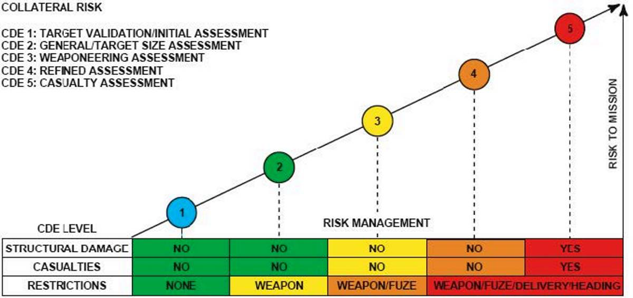 The military defines Collateral Risk in terms of “risk to mission” as depicted in figure #1 below:
The military defines Collateral Risk in terms of “risk to mission” as depicted in figure #1 below:
CDE refers to Collateral Damage Estimate. As we can see from CDE 1: Target Validation/Initial Assessment, the risk management process runs through CDE 5: Casualty Assessment. Three criteria are considered: Structural Damage, Causalities and Restrictions. The Collateral Risk scale/matrix is an escalating scale that focuses on “Risk to Mission” considerations.
The Business Insurance Dictionary includes six definitions of risk:
- A probability or threat of damage, injury, liability, loss, or any other negative occurrence that is caused by external or internal vulnerabilities, and that may be avoided through preemptive action.
- Finance: The probability that an actual return on an investment will be lower than the expected return. Financial risk is divided into the following categories: Basic risk, Capital risk, Country risk, Default risk, Delivery risk, Economic risk, Exchange rate risk, Interest rate risk, Liquidity risk, Operations risk, Payment system risk, Political risk, Refinancing risk, Reinvestment risk, Settlement risk, Sovereign risk, and Underwriting risk.
- Food industry: The possibility that due to a certain hazard in food there will be an negative effect to a certain magnitude.
- Insurance: A situation where the probability of a variable (such as burning down of a building) is known but when a mode of occurrence or the actual value of the occurrence (whether the fire will occur at a particular property) is not. A risk is not an uncertainty (where neither the probability nor the mode of occurrence is known), a peril (cause of loss), or a hazard (something that makes the occurrence of a peril more likely or more severe).
- Securities trading: The probability of a loss or drop in value. Trading risk is divided into two general categories: (1) Systemic risk affects all securities in the same class and is linked to the overall capital-market system and therefore cannot be eliminated by diversification. Also called market risk. (2) Nonsystematic risk is any risk that isn’t market-related or is not systemic. Also called nonmarket risk, extra-market risk, or unsystemic risk.
- Workplace: Product of the consequence and probability of a hazardous event or phenomenon. For example, the risk of developing cancer is estimated as the incremental probability of developing cancer over a lifetime as a result of exposure to potential carcinogens (cancer-causing substances).
RIMS, (The Risk and Insurance Management Society) also has a definition for Enterprise Risk Management (ERM):
Enterprise Risk Management (ERM) is the process of planning, organizing, leading, and controlling the activities of an organization in order to minimize the effects of risk; this includes but is not limited to, financial, accidental losses, strategic, operational and other unrecognized risks.
Enterprise risk management is a strategic business discipline that supports the achievement of an organization’s objectives by addressing the full spectrum of its risks and managing the combined impact of those risks as an interrelated risk portfolio.
The Institute of Internal Auditors (IIA) offers the following:
Enterprise risk management is a structured, consistent and continuous process across the whole organization for identifying, assessing, deciding on responses to and reporting on opportunities and threats that affect the achievement of its objectives.
I could continue with the ISO Standards and other guidance and/or regulatory materials, but that would render this paper nearly useless, as well as, unreadable. However, as we look at these definitions it is readily apparent that “risk” means something very different to those creating the definitions. Yet, we use the term “risk” and expect that our understanding (definition) will be universally comprehended and accepted.
Don Quixote Where Are You?
Creating a universal definition of risk could well be the impossible quest. But, that may be a salvation too; if we begin to carefully communicate our definitions to each other. We can come to an understanding and begin to apply composite or situational definitions of risk based on the criteria that we are using to evaluate the identified risk. What we really need to do is concentrate on how we identify the characteristics of the risk that we are concerned with. We need to then begin to understand and evaluate “collateral risk” in the context of how we intend to buffer the identified risk and in respect to the risk change that results from the buffering against the risk realization.
This may sound complicated but is where an appreciation of “collateral risk” begins to take shape as part of the risk assessment/analysis and overall risk management process. Better to get an understanding of what risks may emerge collateral to the risk that you plan to address and to be prepared to buffer them rapidly.
Creating a Collateral Risk Matrix
Collateral damage is damage to things that are incidental to the intended target. Collateral risk results from the actions taken to reduce (buffer) risk exposure and achieve “risk parity”. By collateral I am referring not to money, but risks that emerge as a result of addressing an identified risk.
As I wrote in my recent article, entitled “Complexity – The Wager: Analysis or Intuition”, risk parity is:
 Risk Parity is a balancing of resources to a risk, threat, hazard, vulnerability (RTHV), etc. You identify a RTHV and then balance the resources you allocate to buffer against the RTHV being realized (that is occurring). This is done for all RTHV that you identify and is a constant process of allocation of resources to buffer the RTHV based on the expectation of RTHV occurring and the velocity, impact and ability to sustain resilience against the RTHV realization. You would apply this and then constantly assess to determine what resources need to be shifted to address the RTHV. This can be a short term or long term effort. The main point is that achieving risk parity is a balancing of resources based on assessment of RTHV realization and potential consequences to the organization. Risk Parity is not static as RTHV and consequences are not static.
Risk Parity is a balancing of resources to a risk, threat, hazard, vulnerability (RTHV), etc. You identify a RTHV and then balance the resources you allocate to buffer against the RTHV being realized (that is occurring). This is done for all RTHV that you identify and is a constant process of allocation of resources to buffer the RTHV based on the expectation of RTHV occurring and the velocity, impact and ability to sustain resilience against the RTHV realization. You would apply this and then constantly assess to determine what resources need to be shifted to address the RTHV. This can be a short term or long term effort. The main point is that achieving risk parity is a balancing of resources based on assessment of RTHV realization and potential consequences to the organization. Risk Parity is not static as RTHV and consequences are not static.
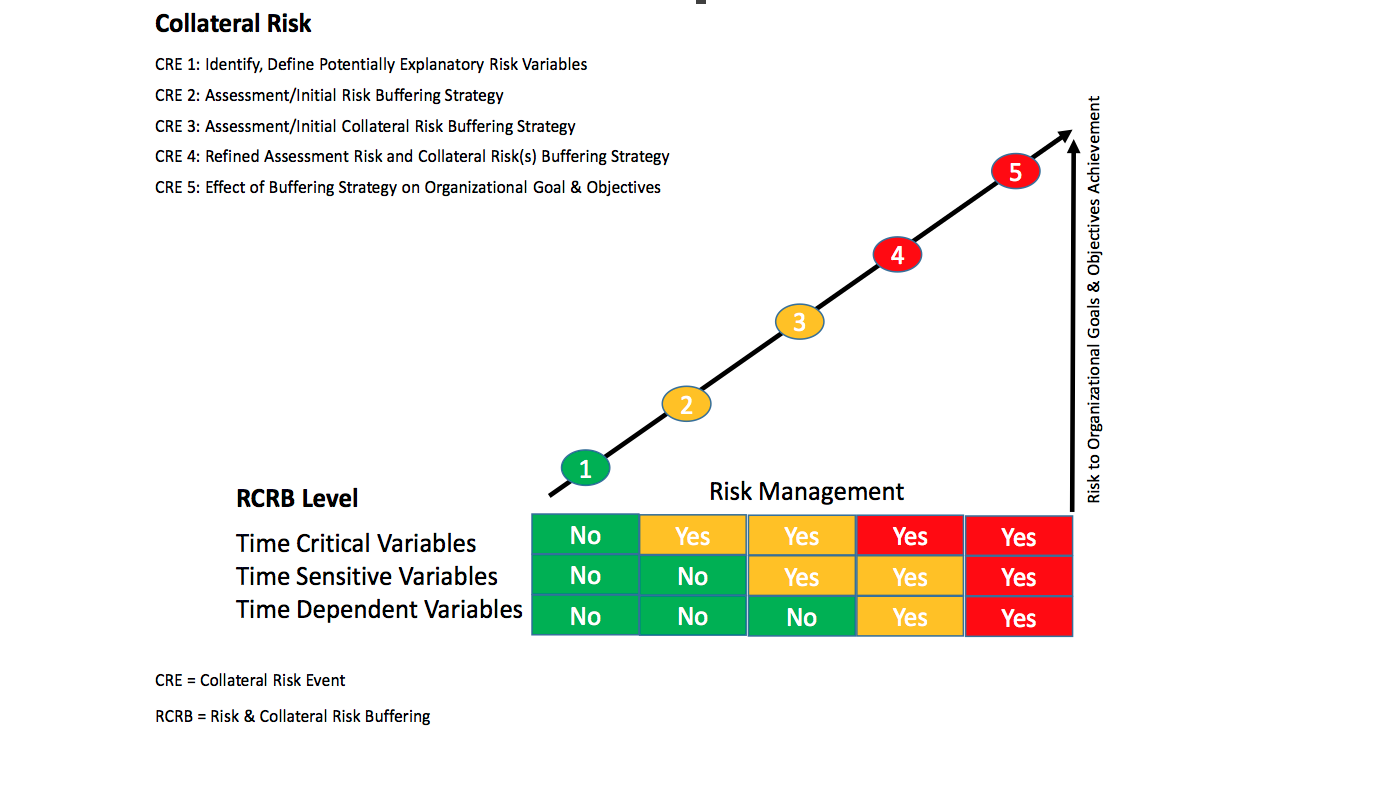
We can use the military matrix as a baseline for creating a Collateral Risk Matrix applicable to business operations. The complexity of the matrix can be adjusted to the degree of in depth risk analysis that the organization chooses to undertake. I also suggest that this can be accomplished with some modification of the LMSCARVERtm assessment tool. Can you identify collateral risk issues with this process? The answer, is yes, and you can custom fit the variables to look at three levels of collateral risk; “Strategic”, “Operational” and “Tactical”. Combine this with an assessment of “time critical”, “time sensitive” and “time dependent” risks and collateral risks and you could end up with a matrix like the one in figure #2, entitled, “Collateral Risk”.
Twelve Key Factors
That are twelve key factors that should be considered as categories for grouping analysis and creating touchpoint identifiers in regard to collateral risk and risk cascade if the primary risk materializes. These are:
| Customers | Human Capital |
| Current Competitors | Suppliers/Vendors |
| Alliances/Partners | Infrastructure (External & Internal) |
| Stakeholders | Government (All levels, National, International) |
| Substitutes/Alternates | Reputation |
| Competitive Intelligence | New Entrants |
These factors can be rank ordered, Key Issue identified, Impact (high, medium, low, short term, long term) assessed, Primary Risk listed and Collateral Risks listed to form an quick reference analysis table. From here “War Gaming” can be utilized to assess risk realization impacts and identify risk cascade and collateral risk realization.
The 12 key factors are depicted below with examples of risk and collateral risk.
| Key Factor | Rank | Key Issue | Impact
(H,M,L) |
Risk | Collateral Risk |
| Customers | 1 | Demand |
H |
Sustainability within current markets | Customer Tolerance Level (CTL), Maximum Tolerable Outage (MTO) |
| Human Capital | 1 | Succession &
Intellectual Value |
H |
Leadership, intellectual capital, sustainability of replenishment pool, key client/stakeholder relationships | Operational impact, Market Share, Sustainability |
| Current Competitors | 2 | Positioning |
H |
Competitive Advantage | Financial, Customer Loyalty |
| Alliances/
Partners |
3 | Interface |
H |
Sustainability, strength in markets served, loyalty, capacity to manage surge | “Value Chain” vetting, Contract structure |
| Suppliers | 4 | Power |
M |
Ability to influence capabilities to provide product/services, readily available alternatives | Continuity of operations |
| Infrastructure | 5 | Internal & External |
M |
Accessibility to; and ability of external infrastructure to meet demand/surges. Limitations of internal infrastructure to meet demand/surges. Cascade effects of failure. | Operations, Financial, Customer, “Value Chain” – Suppliers |
| Stakeholders | 5 | Support Level |
H |
Capability to meet expectations | Financial investments, Market value |
| Government | 6 | Regulatory Drivers |
M |
Number of regulatory agencies and regulatory compliance scrutiny, potential actions – direct impact, potential actions – indirect impact | Customer Tolerance Level (CTL), Financial, Operational |
| Substitutes/ Alternatives | 7 | Threat Level |
L |
Readily available alternatives, differentiating qualities | Financial, Operational, Market Share |
| Reputation | 1 | Image | H | Long term impairment of reputation | Customer Tolerance Level (CTL), Operations, Financial |
| Competitive Intelligence | 2 | Competitive Advantage |
H |
Loss of intellectual capital, data compromise, competitive advantage, market share | Human Capital, Financial, Operations |
| New Entrants | 8 | Threat Level |
L |
Barriers to entry, financial challenges, customer loyalty | Financial, Operations, Human Capital, Customers, Suppliers (“Value Chain”) |
Additional examples of Time Critical, Time Sensitive and Time Dependent criteria are provided below.
Time Critical (Examples):
Time Critical Risks & Collateral Risks can be defined by time periods. For example: 0 – 3 Hours, 0 – 3 Days
- Loss of Critical Infrastructures (External)
- Loss of Critical Infrastructures (Internal)
- Telecommunications/Information Systems
- Transportation (air, land, water)
- Utilities (gas, electric, water)
- Energy Supply
- Critical Services
- Access Denial
- Degradation/Loss of Critical Operations
- Loss/Degradation of Operational Capability
- Loss of Electrical Supply Sources
- Loss of Telecommunications/Information Sources
- Loss/Degradation of Buildings/Occupancy
- Disruption of Transportation
- Disruption of Water Supply
- Disruption of Emergency Services
Time Sensitive (Examples):
Time Sensitive Risks & Collateral Risks can be defined by time periods. For example: 4 – 8 Hours, 4 – 8 Days
- Finance
- Vendor/Supplier
- Business Applications
- Human Resources & Staffing
- Legal Oversight/Documentation
- Transition to Recovery Organization
- Recovery Operations
- Humanitarian Assistance
- Infrastructure Restoration
- Information Recovery & Synchronization
- Resumption of Critical Business Functions
- Full Function Restoration
- Permanent Restoration
Time Dependent (Examples):
Time Dependent Risks & Collateral Risks can be defined by time periods. For example: 8 + Hours, 8 + Days
- Government Relations
- Corporate Relations
- Corporate Image
- Banking & Finance
- Assigned Relocation Sites
- Communication Systems Requirements
- Operations Systems Requirements
- Personnel Requirements
- Documentation of Facilities Recovery
- Assessment of Operations Requirements
- Building Documents/Records Required in an Emergency
- Public Sector Contacts
- Forms and Supplies
- Associated Plans and Information
- Insurance and Risk Management Plan
- Treasury Contingency Cash Plan
- Controller’s System for Tracking Recovery Expenses
- Vendor/Supplier/Consultant List
- Floor space Alternatives outside Main Office
- Records Planning, Storage & Retrieval
Risk & Collateral Risk Analysis (Examples of Areas)
- Corporate Strategy
- Strategic Goals
- Regulatory Compliance
- Competitive Intelligence
- Business Risk Issues
- Human Factors
- Financial Impacts
- “Value Chain”
- Customers
- Vendors, Suppliers
- Outsource Partners
- Systems
- Applications
- Operations
- Infrastructure (Internal)
- Infrastructure (External)
- Product Lifecycle
- Service Offerings
- Succession
- Merger & Acquisition
- Divestitures
- Reorganization
- Natural Events
- Manmade Events
- Cyber Events
- Demand Issues
- Contingencies
- Consequences
Conclusion
In order for any organization to succeed in today’s fast paced, globally interlinked business environment the ability to identify and assess risk and to identify collateral risk needs to be addressed. When you take Management (leadership & decision-making), Planning, Operations, Logistics, Communications, Finance, Administration, Infrastructure (Internal & External), Reputation, External Relations and other dependency issues into account there is significant impact on six areas that I consider critical for organizations – Strategy (Goals & Objectives), Concept of Operations, Organizational Structure, Resource Management, Core Competencies and Pragmatic Leadership (at all levels with a common understanding of terminology).
We live in a world full of consequences. Our decisions need to be made with the most information available with the recognition that all decisions carry with them flaws due to our inability know everything. Our focus should be on how our flawed decisions establish a context for flawed RTHV assessments, leading to flawed plans, resulting in flawed abilities to execute effectively. If we change our thought processes from chasing symptoms and ignoring consequences to recognizing the limitations of decision making under uncertainty we may find that the decisions we are making have more upside than downside.
Bio:
Geary Sikich – Entrepreneur, consultant, author and business lecturer
Contact Information: E-mail: G.Sikich@att.net or gsikich@logicalmanagement.com. Telephone: 1- 219-922-7718.
Geary Sikich is a seasoned risk management professional who advises private and public sector executives to develop risk buffering strategies to protect their asset base. With a M.Ed. in Counseling and Guidance, Geary’s focus is human capital: what people think, who they are, what they need and how they communicate. With over 25 years in management consulting as a trusted advisor, crisis manager, senior executive and educator, Geary brings unprecedented value to clients worldwide.
Geary is well-versed in contingency planning, risk management, human resource development, “war gaming,” as well as competitive intelligence, issues analysis, global strategy and identification of transparent vulnerabilities. Geary began his career as an officer in the U.S. Army after completing his BS in Criminology. As a thought leader, Geary leverages his skills in client attraction and the tools of LinkedIn, social media and publishing to help executives in decision analysis, strategy development and risk buffering. A well-known author, his books and articles are readily available on Amazon, Barnes & Noble and the Internet.
References:
- Apgar, David, Risk Intelligence – Learning to Manage What We Don’t Know, Harvard Business School Press, 2006.
- Jones, Milo and Silberzahn, Philippe, Constructing Cassandra: Reframing Intelligence Failure at the CIA, 1947–2001, Stanford Security Studies (August 21, 2013) ISBN-10: 0804785805, ISBN-13: 978-0804785808
- Kami, Michael J., “Trigger Points: how to make decisions three times faster,” 1988, McGraw-Hill, ISBN 0-07-033219-3
- Sikich, Geary W., Graceful Degradation and Agile Restoration Synopsis, Disaster Resource Guide, 2002
- Sikich, Geary W., “Integrated Business Continuity: Maintaining Resilience in Times of Uncertainty,” PennWell Publishing, 2003
- Sikich, Geary W., “Risk and Compliance: Are you driving the car while looking in the rearview mirror?” 2013
- Sikich, Geary W., ““Transparent Vulnerabilities” How we overlook the obvious, because it is too clear that it is there” 2008
- Sikich, Geary W., “Risk and the Limitations of Knowledge” 2014
- Sikich, Geary W., “Complexity: The Wager – Analysis or Intuition?” 2015
- Taleb, Nicholas Nassim, “The Black Swan: The Impact of the Highly Improbable,” 2007, Random House – ISBN 978-1-4000-6351-2, 2nd Edition 2010, Random House – ISBN 978-0-8129-7381-5
- Law Dictionary: What is COLLATERAL RISK? definition of COLLATERAL RISK (Black’s Law Dictionary)
- <a href=”http://thelawdictionary.org/collateral-risk/” title=”COLLATERAL RISK”>COLLATERAL RISK</a>
- Read more: http://www.businessdictionary.com/definition/risk.html#ixzz3fsb9SYNd
- rims.org/resources/ERM/Pages/WhatisERM.aspx
- theiia.org/guidance/standards-and-guidance/ippf/position-papers/
