The four knowledge cornerstones of project risk management are:
The four knowledge cornerstones of project risk management are:
- Project Management
- Earned Value Management
- Risk Management
- Subcontract Management
Why are these called the four cornerstones? Each cornerstone addresses a primary risk source as shown in Table 1. This article address risk management. The remaining cornerstones will be addressed in separate articles.
Table 1 Knowledge Cornerstones Risk Source
| Cornerstone | Primary Risk Source |
| Project Management | Known risks (scope; schedule; cost; quality) |
| Earned Value Management | Known and unknown (uncertainty and variations) |
| Risk Management | Unknown risks |
| Subcontract Management | Subcontractor risks |
WHAT PROBLEM ARE WE SOLVING IN THIS ARTICLE?
The problem we are solving in this article is providing you with a basic understanding of the risk management process. The definition and explanation of a risk, description of what risk management means, and a discussion of the methods used to identify risks are topics included in this chapter.
WHY IS IT IMPORTANT TO YOU?
Projects typically fail due known and unknown risks. Known risks are addressed primarily by applying effective project management methods and principles as well as EVM. Unknown risks are the uncertainty and variances that surround all projects. It is important for you to understand the risk management process and gain the knowledge and skills to identify risks on your project to mitigate the uncertainties and variances and pave the way for a successful project. Future work will become more projectized. As a result, it behooves you to be adept at-risk mitigation and how it is done.
WHAT IS THE RISK MANAGEMENT PROCESS?
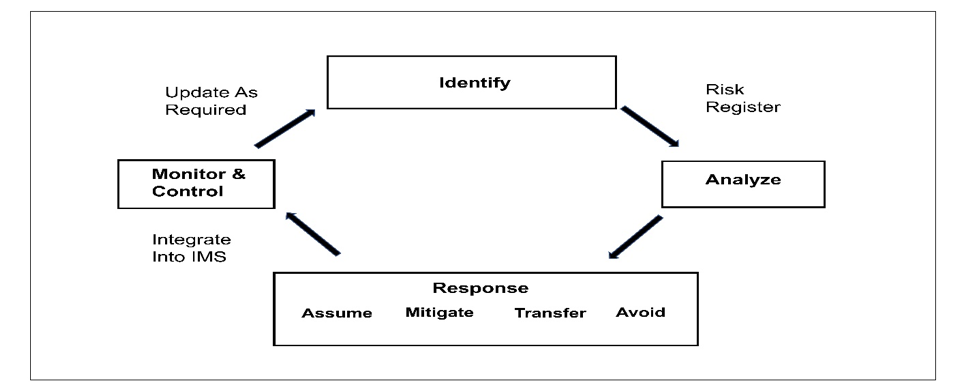
Figure 1 shows the risk management process. It comprises four basic steps. They are: identify the risks; analyze the risks; risk response; and monitor/control the risks.
Figure 1 Risk Management Process
Table 2 shows some common techniques for identifying risks.
Table 2 Risk Identification Techniques
| Technique | Comment |
| Brainstorming. | Group members build on each other’s ideas |
| Surveys | List of questions are developed to seek out risks |
| Interviews | An effective way to determine risk areas |
| Working groups | Good way to analyze an area to surface risks |
| Documented knowledge | Collection of data/ information about a risk area |
| Historical information | Similar to documented knowledge but widely accepted |
| Engineering templates | These templates are intended as general guidance to accomplish a top down assessment of activities. |
| Work Package (WP) level assessments | The most effective technique to identify risks is at the WP level. The WP manager is the most knowledgeable team member to assess the risks for his/her task. |
Analyze risks
There are two basic types of analysis. They are: qualitative and quantitative methods. The qualitative method is more commonly used because, with the exception of mega-projects, there is usually insufficient data to perform a valid quantitative analysis. Table 3 shows an example of qualitative risk levels. The levels are subjectively chosen based on experience and typically approved by the project manager.
Table 3 Qualitative risk levels
| Level | Probability of Occurrence (%) | Impact of Occurrence |
| High | 41-50 | Very likely to occur. Has occurred in past projects. |
| Medium | 31-40 | Likely. Possible to occur. |
| Low | 10-30 | Unlikely to occur. |
Response (Handled)
Once the risks (and opportunities) have been identified, the next step is to determine how they will be handled (or responded to). Risk response (handling) options include:
- Assume
- Mitigate
- Transfer
- Avoid
Assume
In this case, the risk is acknowledged but no action is taken because the priority is low and it is not possible or cost effective to address it. For example, if one of your key suppliers is located in a flood zone, there is a risk a flood will happen resulting in schedule and cost impact to your project.
Mitigate
Mitigating a risk is the most common technique primarily due to the fact the other three techniques are not that common. Mitigation action is taken to reduce the probability of occurrence and impact on a project. There are many ways to mitigate a risk depending on what the risk is. For example, redundancy can be added to a system to increase the reliability and reduce the probability of occurrence.
Transfer
This handling technique involves transferring the risk to another party. For example, fire or flood risks can be transferred to an insurance agency.
Avoid
Avoidance of a risk is when the project team takes actions to eliminate a risk. For example, if one of your major suppliers may go on strike in the middle of the contract, avoiding the risk could be done by splitting the contract between the subject supplier and another supplier.
Control and Monitor
Project risk control and risk monitoring is where you keep track of your risk responses (mitigation plans) performance against the plan usually on a monthly basis. Earned Value Management is a very useful tool to control and monitor risks.
Summary
Risk management is a knowledge cornerstone of project risk management because it is essential to managing unknown risks. The future of work is based on new technologies such as: Robotics; Artificial Intelligence; and Big data. New technologies bring new unknown risks. Risk management will be more important in future work to manage these risks.
Post Note
 I authored a new book entitled ‘Project Risk Management’. How to manage known and unknown risks is discussed in detail in my book. The book contains much more detail, examples, and risk stories. It is easy to read and understand. Visit my website https://projectriskmanagement.info/. It includes a link to Amazon and my book as well as the technical papers I have written over time.
I authored a new book entitled ‘Project Risk Management’. How to manage known and unknown risks is discussed in detail in my book. The book contains much more detail, examples, and risk stories. It is easy to read and understand. Visit my website https://projectriskmanagement.info/. It includes a link to Amazon and my book as well as the technical papers I have written over time.
Bio:
Currently John is an author, writer and consultant. He authored a book entitled ‘Project Risk Management. He has written numerous risk papers and articles. He writes a risk column for CERM.
John earned a BS in Mechanical Engineering and MS in Engineering Management from Northeastern University. He has extensive experience with commercial and DOD companies. He is a member of PMI (Project Management Institute). John has managed numerous large high technical development programs worth in excessive of $100M. He has extensive subcontract management experience domestically and foreign. John has held a number of positions over his career including: Director of Programs; Director of Operations; Program Manager; Project Engineer; Engineering Manager; and Design Engineer. He has experience with: design; manufacturing; test; integration; subcontract management; contracts; project management; risk management; and quality control. John is a certified six sigma specialist, and certified to level 2 EVM (earned value management
If you want to be a successful project manager, you may want to review the framework and cornerstones in my book. The book is innovative and includes unique knowledge, explanations and examples of the four cornerstones of project risk management. It explains how the four cornerstones are integrated together to effectively manage the known and unknown risks on your project.