My client Saudi Arabian Aramco is the world’s most-valuable oil producer has confirmed that some company files were leaked after hackers reportedly demanded a $50 million ransom, this is not the first time, last time the total cost of the Incident cost one $ Billion
My client Saudi Arabian Aramco is the world’s most-valuable oil producer has confirmed that some company files were leaked after hackers reportedly demanded a $50 million ransom, this is not the first time, last time the total cost of the Incident cost one $ Billion
Ransomware attacks have tripled over the past year. Even if your organization is operating in full compliance with all laws and regulations, paying a ransom to a sanctioned cybercriminal in response to an attack is prohibited in most countries, these are risks we cannot afford to take, we need to discuss and implement best practices for your risk-based compliance program to be better prepared for escalating cybersecurity threats, including how to:
- Identify trends and the latest tactics used by ransomware groups
- Understand the nature, evolution, and scale of the cyber and ransomware compliance landscape
- Examine key considerations in maintaining robust compliance and managing risk in the context of these evolving issues
- Assess regulatory expectations and guidance in the cyber and ransomware space
“Aramco recently became aware of the indirect release of a limited amount of company data which was held by third-party contractors,” the Middle Eastern oil major said in an email.
“We confirm that the release of data was not due to a breach of our systems, has no impact on our operations, and the company continues to maintain a robust cybersecurity posture.”
Aramco reported earlier that 1 terabyte of Saudi Arabian Oil Co. data had been held by an extortionist, citing a web page it had accessed on the darknet. The state-owned driller was offered the chance to have the data deleted for $50 million in cryptocurrency.
The global energy industry has seen a ramp up in cyber attacks with Colonial Pipeline becoming the most visible of late. The oil and gas industry, which includes the companies that own wells, pipelines, and refineries, has long been a laggard in security spending, according to consultants.
In 2012, while working at the Aramco Executive Airport, the company blamed unidentified people based outside the kingdom for a hack against the oil giant that aimed to disrupt production from the world’s largest exporter of crude Oil. The so-called “spear-phishing” assault destroyed more than 30,000 computers within hours, the operator simply put a USB memory stick in his computer, it moved across the network with lightning speed. A spokesman for the Interior Ministry declined at the time to identify any of the “several foreign countries” from which the attack originated, the Incident crippled production, including the airport, as they no longer had the manual systems, but had to buy another 30,000 computers.
The Middle East has previously been a magnet for some of the world’s costliest hacks, PricewaterhouseCoopers LLP said in a 2016 report.
Energy companies from electric utilities to power-grid operators to pipeline operators have warned that cyberattacks are becoming more and more prevalent. The largest U.S. power grid operator, PJM Interconnection LLC, has warned regulators that it’s facing increasing attacks, the following are recent headline grabbers from around the world.
Hackers Nabbed $1.3 Billion in Ransom Over 2 Years,
Hacker hacking, Banks Told to Be Vigilant on Cyber Risk as Russia Tensions Rise
Russia’s Crypto Space Blockchain and Crypto-currencies Conference
Cybersmart’s Hits 300% Yearly Returns for Backers Such as Sequoia
Microsoft Considers Pursuing a Deal for Cybersecurity Firm Mandiant
Pentagon Cyber Official Resigns After Security Clearance Dispute
Homeland Security Forms Board to Examine Hacks Like NTSB Probes Plane Crashes
Dept. Of Homeland Security HQ As Congress’ Spending Plan Funds Agency Only Through February
Ransomware Attack in Germany Tied to Colonial Pipeline Hackers
DeFi Project Known as Wormhole Hit with a Potential $320 Million Hack relates to DeFi Project Known as Wormhole Hit with a Potential $320 Million Hack
Thales Weighs Partnering with Private Equity on Atos Deal
Diplomatic Flurry Intensifies in Kyiv, Moscow: Ukraine Update
Bloomberg News
Careers Made in NYC Advertise Ad Choices Help
Safety Projects International Inc is widely regarded as one of the leading integrated risk management, crisis response, OHS&E consulting, and global protective solutions company, serving the world’s most influential people, disruptive brands, and prominent organizations. Championed by our highly skilled team of intelligence analysts, we offer highly specialized services, 24/7 security and consulting,
Ransomware, Phishing, and Malware: 4 ways to Defend and Respond to External Threats
- Improve detection with behavioral analytics
Behavioral analytics tracks, collects, and analyzes data to create a baseline of normal asset and user activity. With a picture of normal created, behavioral analytics attaches a score to users and assets based on their activities that provides an analyst with additional context to detect an external threat. These behavioral analytics can provide the following capabilities:
Additional incident detection beyond rules and signature identifies abnormal and high-risk activity above and beyond predefined correlation rules or threat patterns. The result is higher confidence threat detection and fewer false positives.
Machine-built timelines for security incidents can stitch together related security events into a contextual timeline that shows a security incident, spanning multiple users, IP addresses, and IT systems.
Dynamic peer groupings not only performs behavioral baselining of individual entities, but it also dynamically groups similar entities (such as users from the same department or IoT devices of the same class), to analyze normal collective behavior across the entire group and detect risky behavior.
Lateral movement detection can detect attackers as they move through a network using different IP addresses, credentials, and machines, in search of sensitive data or key assets. It ties together data from multiple sources to connect the dots and identify and stop an attacker’s journey through the network.
- Quickly identify phishing attacks
Phishing attacks typically involve social engineering, which is the use of deception to manipulate users into divulging their credentials by clicking a weaponized link or opening a malicious attachment. Phishing is an entry point for many attacks and can lead to malware infection, lateral movement, account takeover, data exfiltration, and more. With the high volume of threats and new phishing campaigns appearing daily, security teams require a means to stay ahead of attacks.
There are many programs that detect phishing attacks and provides a full list of compromised users and assets for investigation.
A phishing checklist guides analysts to answer key investigation questions and prescribes a comprehensive list of response actions.
The Phishing Playbook automates key workflows, such as leveraging threat intelligence to check the reputation of links or attachments in emails.
- Additional detection for malware attacks
A favorite tool in an attacker’s toolbox continues to be malware — from Trojans to more destructive malware families. Detecting and preventing 100% of malware is not feasible, so it is critical that organizations employ secondary behavior-based detection capabilities to catch malware that slips past their primary prevention layer.
Given its ability to carry out any number of tasks and the virtually unlimited variants available, attackers will use malware across the entire attack chain, from infiltration to data exfiltration. many detection models can identify never before-seen malware before it has an opportunity to carry out its objective.
The system automatically detects abnormal behavior associated with malware, such as processes executed or anomalous file activity.
Smart Timelines and malware checklists help analysts investigate threats by answering questions like, “Has this malware been found on other machines?”
The Malware Playbook automates key workflows, like detonating a file in a sandbox.
- Detect, identify, and remediate ransomware activity
According to IBM’s 2021 DBIR report, incidents of successful ransomware attacks doubled from 2020, making up 10% of all attacks publicly reported. Attackers continue to deploy ransomware because it returns a profit. With ransomware-as-a-service available on the dark web, attackers no longer need to be proficient in writing malicious code. In a matter of minutes, virtually anyone can initiate a ransomware attack that could pay for itself in hours or days. Relying solely on indicators of compromise (IoC) leaves you vulnerable and even the best malware detection and prevention tools on the market can fail to identify a file as malicious ransomware.
To mitigate these cases, organizations must have a secondary behavior-based detection method, coupled with an automated recovery and response mechanism that enables them to minimize damage and return to a trusted state fast without paying any ransom or losing data.
Many detects techniques, tactics, and procedures (TTP) consistently seen across ransomware attacks, providing visibility into assets with vulnerabilities or misconfigurations that attackers may exploit.
Analysts can quickly investigate and respond to any threats with incident timelines, a guided checklist, and automated playbooks to ensure they intervene in the early stages of a ransomware attack and prevent payday.
The external threats use case package is particularly helpful for teams that can benefit from pre-built content and automation is simple to implement with no additional licensing or configuration required, significantly accelerating time to value.
Due to global footprints, remote workforces, and cloud adoption, today’s complex organizations have many potential access points for cyberthreats. Securing an organization can often feel like a precarious climb.
Your companies Security incident response and threat intelligence service should apply proactive threat intelligence, incident response, threat hunting, and consultation services to help your organization prepare for, detect, and respond to whatever cyber incidents come your way.
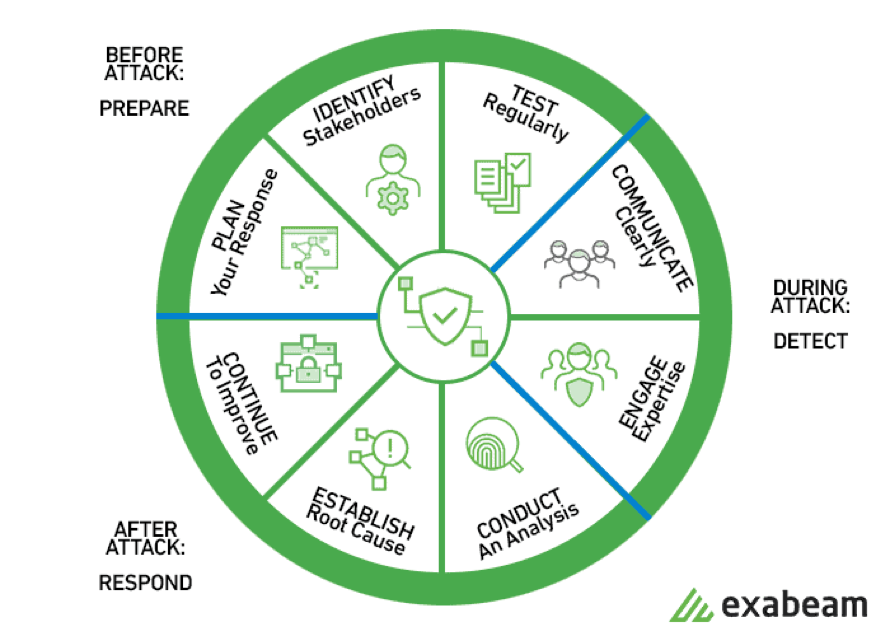
Being prepared with solid incident response procedures in place is the first defense strategy to avoid operating in crisis mode.
With well-planned incident response and threat intelligence services, your organization can identify potential threats before they strike. Rapid response during a breach
The reality of cybercrime is that it is more likely its more a case of when and how bad will an Incident be for an organization, rather than if it will occur. (Pomfret) and while you cannot control when an attack will happen, you can limit its impact through effective preparedness and a detailed incident response plan.
Dr Bill Pomfret; MSc; FIOSH; RSP. FRSH;
Founder & President.
Safety Projects International Inc, &
Dr. Bill Pomfret & Associates.
26 Drysdale Street, Kanata, Ontario.K2K 3L3.
www.spi5star.com pomfretb@spi5star.com
Tel 613-2549233