In September 2022 the National Institute of Standards and Technology (NIST) issued NIST IR 8286C. (1) As the C indicates, this is the third such cybersecurity risk management standard issued by NIST. NISTIR 8286A and 8286B provide guidance to stakeholders on assessing and managing cybersecurity risk in conjunction with Enterprise Risk Management (ERM) processes. This piece looks at the guidance provided under NIST IR 8286C.
In September 2022 the National Institute of Standards and Technology (NIST) issued NIST IR 8286C. (1) As the C indicates, this is the third such cybersecurity risk management standard issued by NIST. NISTIR 8286A and 8286B provide guidance to stakeholders on assessing and managing cybersecurity risk in conjunction with Enterprise Risk Management (ERM) processes. This piece looks at the guidance provided under NIST IR 8286C.
Purpose
NIST IR 8286C provide guidance for all sectors, public and private, on how to integrate Cybersecurity Risk Registers (CRR) in a “holistic manner” into the organization’s ERM process, specifically the enterprise risk register and enterprise risk profile. (The risk register is a prioritized compilation of the risks the organization faces. The risk profile is the assessment of the major risks an organization faces and the likely impact.)
Audience
As noted above, the guidance is for all sectors. However, it important to note two things. First, NIST guidance is essentially a mandate for federal agencies. This has been established in several Presidential Executive Orders. Most recently in the Executive Order on Improving the Nation’s Cybersecurity. (2) Second, Executive Orders, M-22-12, and the Food and Drug Administration (FDA) Risk Management Plan Draft Guidance, both stress the need to integrate operational activities with ERM. (3) Both also require federal agencies to assess risks to their program activities, which includes grants, loans, and contracts.
While the focus of the executive orders is on federal agencies, the FDA risk management plan touches on the private sector. Further, NIST’s cybersecurity risk integration plan, links cybersecurity with ERM. The rational is clearly stated in IR 8286C. “The importance of information and technology risks to the enterprise risk posture makes it critical to ensure broad visibility about risk-related activities to protect enterprise reputation, finances and objectives.” (4)
Consequently, IR 8286C can be seen as something stronger than a recommendation for all public and private sector organizations which accept money from the federal government.
Structure of NIST IR 8286C
NIST IR 8286C’s focus is on integrating Cybersecurity Risks into the broader ERM process. While the integration process and the development of a CRR is discussed, there is a reliance on the prior two reports to more fully describe the ERM implementation process. (For a step-by-step review of what governments at all levels around the world are doing at each step in the ERM implementation process, see my book Enterprise Risk Management in Government: Implementing ISO 31000:2018. It is available on Amazon.)
To facilitate the integration process NIST IR 8286C emphasizes three main actions. These are: 1. Aggregation of Cybersecurity Risk Information, 2. The integration of the Cybersecurity Risk Register into the Enterprise Risk Register and 3. Establishing the organization’s Risk Profile.
Aggregation
In this activity all the risks associated with Cybersecurity are identified. The identified risks come from each component and level of the organization. In other words, it is enterprise wide.
Where duplicates are present, they are combined. Where there are differences in perspective or description, a common understanding sought. Once the risks are aggregated, they are scored based on their impact and probability of occurrence.
The scored list become the CRR. This register is then integrated with the risk registers from the other functional activities that comprise the enterprise.
Integration
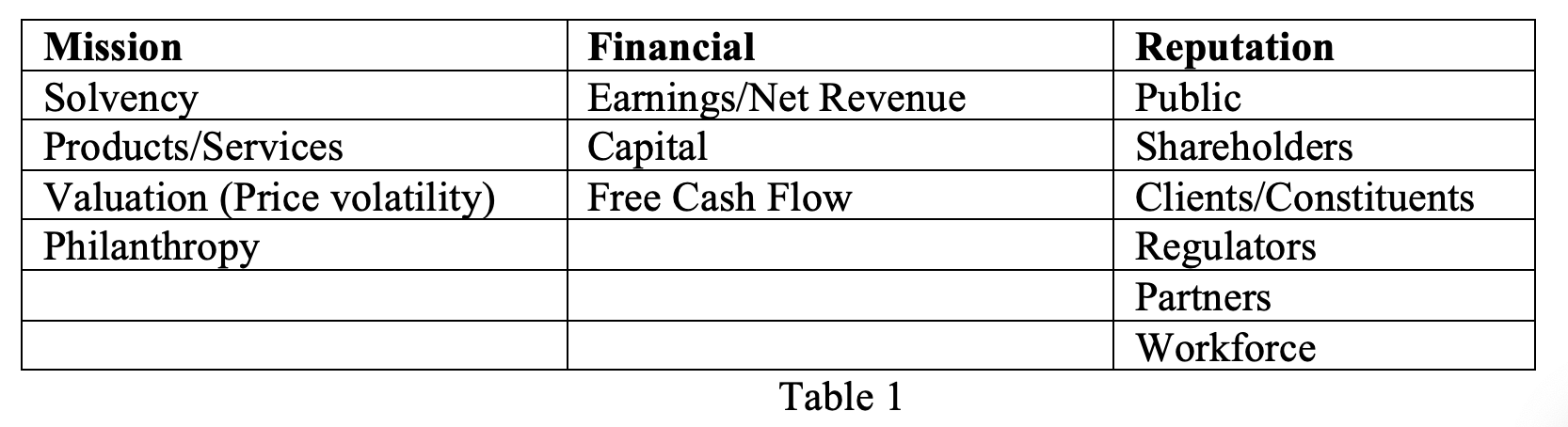
NIST lists four enterprise-wide risk functional activity. These are Mission, Financial, Reputational and Cybersecurity. NIST defines the first three function as follows:
Mission: Risk conditions that affect the enterprise’s ability to achieve objectives.
Financial: Practices that represent exposure to net income, capital, cash flow, and solvency factors, including appropriations and investments.
Reputation: Considerations that might be measurable through key stakeholder surveys or sentiment analysis. (5)
Table 1 shows the risk areas under each activity.
Enterprise Risk Profile
The Enterprise Risk Profile (ERP) is the end goal of the process. It is described as follows:
“The ERR informs the ERP once the risks are as prioritized at the highest level of the Risk Management Function in the enterprise … The ERP is a subset of carefully selected risks from the largest ERR. As the federal ERM playbook points out, there is no single best way to document a risk profile.” (6)
In general parlance, the ERP is the prioritized strategic risk register of the enterprise as determined by the members of the C-suite. It reflects the assessment of the key mission, financial, reputational, and cybersecurity risks the organizational faces and the approaches the organization is taking to mitigate these risks.
Summary
NIST has released the third cybersecurity guide. It is designated NIST IR 8286C. Its specific focus is the integration of cybersecurity risk management into the overall ERM process of the organization. While NIST IR 8286C is considered a guide, it is a mandate for federal agencies. Thus, any organization which takes money from the federal government will likely be encouraged to follow the guidance laid out in NIST IR 8286C and integrate CRR with ERR to produce the ERP.
Endnotes
1.NIST, 2022, Staging Cybersecurity Risks for Enterprise Risk Management and Governance Oversight, NIST IR 8286C, https://www.nist.gov/search?=+8286C
- U.S Government, 2021, Executive Order on Improving the Nation’s Cybersecurity, May 12, https://www.whitehourse.gov/briefing-room/presidential -action/2021/05/12/executive-order-on-improving-the-nations-cybersecurity.
- Kline, James J. 2022, Biden Administration Pushes ERM, CERM Insights # 377, Portland Oregon.
- NIST, 2022, Op. cit. Page 1.
- Ibid, Page 13.
- Ibid, Page 14.
BIO
James J. Kline has a PhD from Portland State University. He has worked for federal, state, and local government. He has consulted on economic, quality and workforce development issues. He has authored numerous articles on quality and risk management. His book “Enterprise Risk Management in Government: Implementing ISO 31000:2018” is available on Amazon. He edited “Quality Disrupted” which is also available on Amazon. He can be contacted on LinkedIn or jamesjk1236@outlook.com