On October 27, 2022, The Association of Federal Enterprise Risk Management (AFERM) in conjunction with Guidehouse released the results of the eighth consecutive survey of federal agencies on their Enterprise Risk Management (ERM) efforts. This piece looks at the survey results.
On October 27, 2022, The Association of Federal Enterprise Risk Management (AFERM) in conjunction with Guidehouse released the results of the eighth consecutive survey of federal agencies on their Enterprise Risk Management (ERM) efforts. This piece looks at the survey results.
Survey Respondents and Questionnaire
The survey covered 62 federal agencies, including 16 cabinet agencies. Half of the respondents indicated the presence of a chief risk officer or having an ERM office. The survey was conducted between June 14 and July15, 2022. (1)
Survey Results
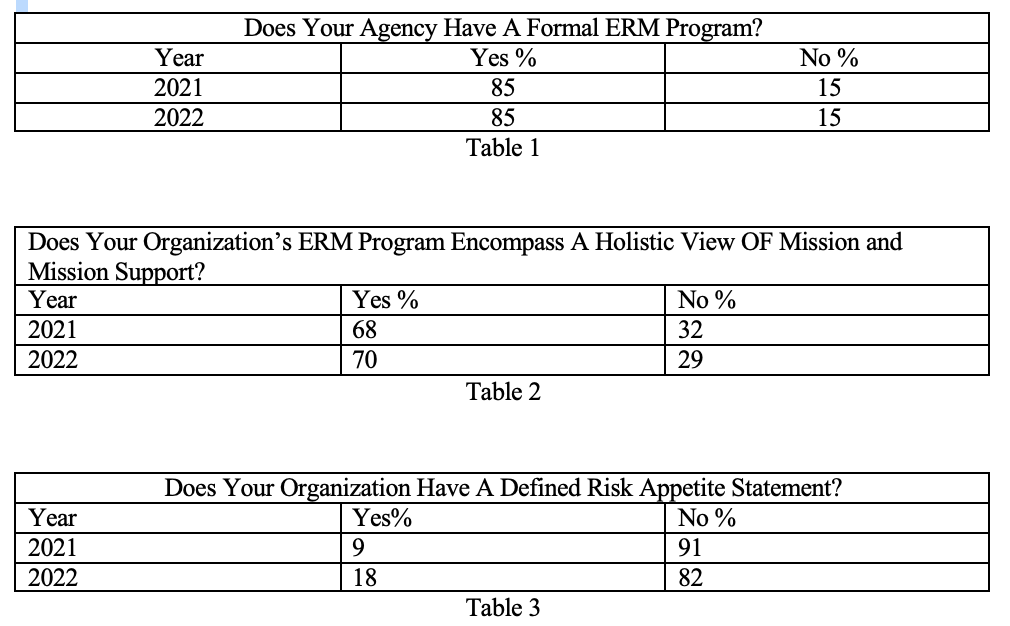
The three tables below show the key findings from the survey.
Overall, the survey indicates that the number of federal agencies using ERM has not substantially changed since 2021. However, there has been movement in the number of agencies taking a holistic approach to ERM and a larger gain in the number having a defined risk appetite statement.
A lack of resources, both financial and human, may be a major contributor to the stalling of ERM’s adoption. Sixty-five percent of the respondents indicated that their overall budget had stayed the same as last year. That is 10% more than those indicating a flat budget in 2021. In addition, 82% of 2022 respondents indicated that their ERM workforce consisted of ten or fewer people (including contractors).
As with past surveys, correlations were drawn between application characteristics and ERM implementation.
Correlations Which Positively Impact ERM Implementation
The survey identified five characteristics which positively affect ERM implementation. These are listed below in order of importance.
- Organizations which incorporate risk management into the performance plans of all members of the Senior Executive Service (or equivalent).
- Organizations where the ERM program leaders spend more than 50% of their time on ERM.
- Organizations with longer duration ERM programs (operating 3 or more years).
- Organizations in which the ERM program reports directly to the Agency Head or Deputy.
- Organizations with a Chief Risk Officer (CRO) in charge of the program.
The responses indicate that ERM implantation takes effort. The longer it is implemented the more it takes hold in the everyday operational activities. The implementation effort can be facilitated by the organizational structure. Having a CRO helps. As does having the CRO reporting directly to the Agency Head or the Deputy.
Since the environment federal agencies work in is dynamic. Doing risk management can take time. Having an ERM leader who spends more than 50% of the time on risk assessment and mitigation is also positively correlated with ERM implementation.
Along these lines, respondents were asked to identify both the significant risks their agency might face in the next 3 years and what other risks should be added to the organization profile.
Looking Ahead
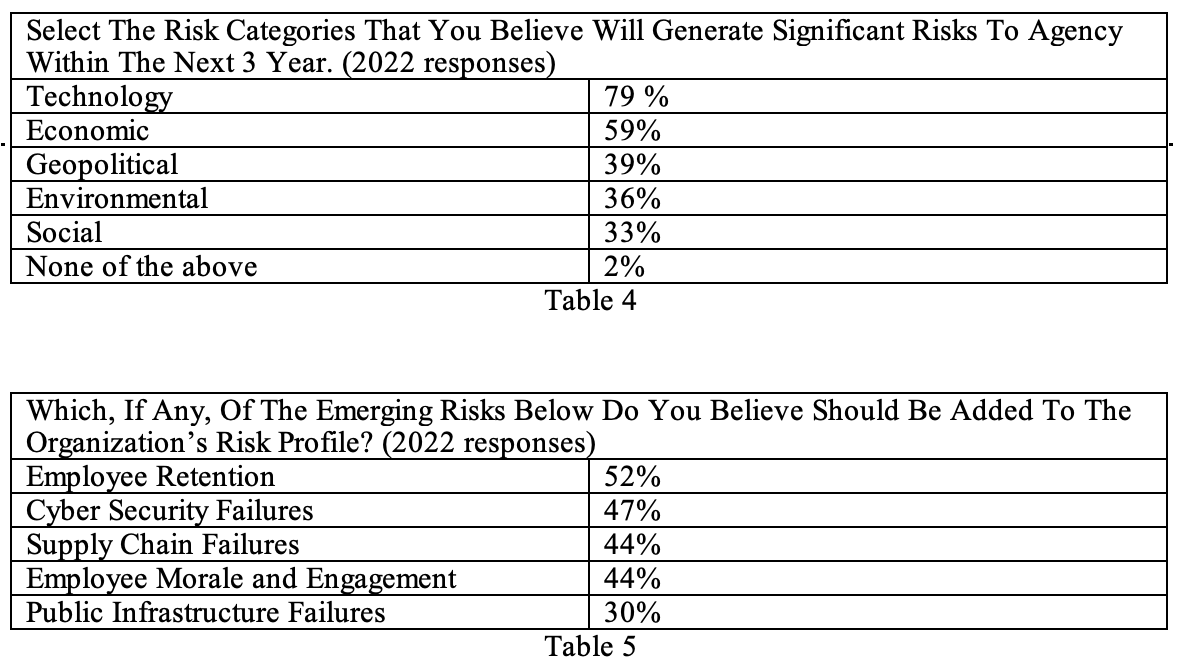
The two tables below show the risks anticipated in the next three years and those which should be added to the risk profile.
As noted in Table 4, risks related to Technology are expected to be more important over the next three years. Unfortunately, given the diversity of the areas federal agencies focus on, the broadness of the terms means little. For instance, technology could mean anything from a new toaster to a sophisticated computer network. When one looks at Table 5 and the belief that Cyber Security Failure should be added to the risk profile, it is likely that computer related technology is at least part of the risk under Technology. The other categories listed in Table 4 are equally general and obscure. Thus, they provide little assistance to management.
Table 5 on the other hand, provides substantial information on areas which management needs to focus on. For instance, Employee Retention and Morale and Engagement are related risks. If morale is high and employees feel engaged, retention becomes less of an issue. While Cyber-security and Supply Chain risks are more complex, any adverse impact can extend beyond the federal government boundaries. Because of their significant adverse impact, these risks should already be part of every agency risk profile.
Discussion
The survey indicates that the growth of ERM has not changed from 2021. Further, with only eighteen percent having a defined risk appetite, most federal agencies have a long way to go before ERM implementation can be considered successful. However, the fact that 85% of the respondents indicate they have ERM program means that federal agencies are aware of ERM. This awareness will likely result in risk management concerns filtering into the rules and regulations promulgated by federal agencies. (I discuss a number of these in CERM Insights #404, #378 and #377.)
The list of risks likely to impact federal agencies in the next three years is very broad and almost worthless to management. The risks which should be added to the existing risks identified by agencies, on the other hand, are very useful. Employee retention (52%) and Employees Morale and Engagement (44%) are interconnected. If employee morale is high and employees feel engaged, retention is less of a problem. Cyber Security Failures (47%) and Supply Chain Failures (44%) pose more serious risks. Given that most government operations are computerized, including supply chain management, any cyber security breach can have an adverse impact on federal agencies, and any organizations linked digitally to federal operations.
Endnotes
- Guidhouse and AFERM, 2022, 2022 AFERM-Guidehouse Enterprise Risk Management Survey: Eighth Annual Survey Results, October 27, https:guidehouse.com/news/energy/2022/guidehouse-and-aferm-2022-survey-results-revel-state-of-erm-in-federal-government?lang=en.
BIO
James J. Kline, Ph.D., CERM, is the author of numerous articles on quality in government and risk analysis. He is the author of Enterprise Risk Management in Government: Implementing ISO 31000:2018, and the editor of Quality Disrupted. Both are available on Amazon. He can be reached at jeffreyk12011@live.com.